Selected Job Profile
Cybersecurity analyst
Role: The role of the cybersecurity specialists is to maintain the security of the computer information systems majorly against cybercrimes that involve denial of service attacks, phishing sites, viruses, hacking, and malware. The roles and responsibilities of the cybersecurity analyst includes a number of activities to take care of, some of them are mentioned below:
- Generating reports for technical as well as non-technical shareholders.
- To track and respond to “pharming” activity and ‘phishing’ emails and websites.
- To keep updated with the latest technology and security developments.
- Research about emerging risks about cybersecurity and methods to handle those threats.
- Monitor attacks, unusual activities, intrusions and unauthorized or illegal activities.
- Give guidelines and advice to the staff on issues such as unwanted or malicious and spam mails.
- Make plans for disaster recovery while security breaches.
- Help with the maintenance, creation, as well as delivery of awareness trainings about cyber security to the colleagues.
- Evaluate and test for the security products.
- Upgrade existing security systems by designing the new security systems.
- Engaged in Ethical Hacking for simulating security breaches.
- Investigating security alerts and provide response.
- Identifying potential weakness in the system and implement measures accordingly such as firewalls and encryptions.
- Monitoring identity and access management.
Qualifications
It is not necessary to have a degree to enter this profession of cyber security analyst. You just have to be skilled enough to work up to cyber security role.
Majority of the employer recruit for a position of a graduate, they prefer or require, a graduate degree in science or technology or may be in Engineering (Narayanan, et al., 2017).
Exact requirements may vary from employer to employer. More relevant degree subjects include:
- Computer science
- Information security
- Network Engineering
- Information security
- Network security
- Information technology
- Software Engineering
Your degree will not value any longer as once you start gaining experience, and the employers will be interested in what projects you’ve worked upon, not in your qualification. You may choose relevant subject area to undertake further studies.
Some employers can sponsor you to undergo relevant master’s degree. You can also choose a certification related to cyber security to get a proof of a knowledge you’ve gained.
Career Prospects
Cybersecurity is one of the rapidly developing field and currently there is a skill shortage. Job scope is good for the skilled and experienced people. One will start with an entry or junior level cyber security job. After gaining the experience of several years you could get progress into senior cyber security roles like cyber security analyst/ cyber security consultant (Palmer, et. al., 2019).
After having a significant expertise in the same field, one might be able to get progress in high level leadership roles as well as managerial roles, and eventually ending up with becoming a head or director of cyber-security. Achieving certifications relevant to the cyber security might be help in your development as most employer consider these roles as important.
Self-employment can be considered as a choice, but mostly people firstly gain expertise in the relevant field. one could set a company which will provide cyber security services or can individually work as independent cyber security consultant.
Application letter
Dear Mr. XYZ
PQR security Consulting
Sub: Job Application
Sir,
I am looking for a job in field of cyber security analyst in a reputed company and I would like to work in your company. I think I have all necessary skills along with experience required by your company and would be glad to make valuable contribution in success of your company. As indicated by my resume I have more than 5 years of experience in field of cyber security. I have worked as team leader in national division of cyber security for more than 3 years and has done many projects as an analyst of cyber security. I have earned my degree of bachelor in field of computer science with very strong mathematical background. Previously I was working in division of national cyber security for so many years I have learned many things there and gained experience in many fields such as how we can secure any computer system like large server, and mainframe, from external as well as internal attacks. This is an obvious thing that analyst of cyber security needs continuous education about field with time because there are a lot of hackers can be seen in world and they keep finding new methods of infiltration of computer systems. An analyst of cyber security must stay ahead of them from one step so that they can’t infiltrate computer systems easily.
My main strengths lie in effectively leading a team and problem solving and I accepts challenges created by hacker to get into my computer system very gladly and I always stay ahead of them. I have strong communication skills required for leading a team and along with that my English is good so that I will not find any troubles in making necessary reports and documents. I have sharp analytical skills and can solve very complex problems easily. I have very good time management skills and able to meet deadlines for assigned projects. I can assist staff in errors understanding and glitches repairing. I have excellent knowledge about use of computer programs aiming in direction of digital security. I will love opportunity of working in your company as analyst of cyber security.
I am very certain that your company will find all of my talents and expertise up to the mark for an analyst of cyber security. Please schedule an interview according to your convenience I am expecting a person to person or a telephonic interview to be scheduled as soon as possible. I am excited to meeting you and to work in your company and I also thank you for your valuable time and for your considerations.
Sincerely,
XYZ
Major criteria of selection
Key criteria of selection in any company as an analyst of cyber security some major points must be kept in mind and there are some basic as well as advanced requirements like licensing requirements, experience, education requirements etc. for working as analyst of cyber security in any company. All these requirements are mentioned below with full description:
- Person’s bachelor’s degree must be in field of computer science or in field of information system or there can be equivalent work experience or education (Washington, 2017).
- Experience should be more than 4 years. In field of cyber security with good mathematical background.
- Person must have done advanced certification courses such as GCIA, SANS GIAC, GCIH, CASP or CISSP and special training of SIEM along with certification.
- Certification of Hold DoD 8570 IAT of 2nd level (CE + Security) at date of starting.
- An analyst must have advanced understanding in fields of TCP/IP, Basic networking
- Protocols and ports, flow of traffic, administration system, OSI model, in depth defence and elements of common security.
- High level of experience in analysing high-volume logs, network’s data and many other artifacts of attack in incident investigation’s support.
- Experience in scanning solutions of vulnerability.
- Familiarity in program of vulnerability program of DOD information’s assurance.
- Good knowledge of any of following: HIPS, anti-virus, complete packet capture, ID/PS, forensics which are host based, forensics of network, and security of RSA.
- Complete and in-depth architecture knowledge, knowledge of engineering, and all operations of minimum 1 enterprise ‘s SIEM platform (for e.g. Nitro or McAfee manager of enterprise security, Radar, Log Logic, ArcSight, Splunk.
- Experience in deploying along with developing signature. (e.g. Snort, YARA, HIPS, Suricata).
- Complete understanding of Operating system (i.e. IOS, Android, Windows) and mobile technology along with VMware technology, and basic Unix commands with Unix.
Skills required for cyber security
- System administration: An analyst of cyber security must posses’ skills of managing so many systems such as software, hardware, workstations, effectively and efficiently.
- Network security: an analyst of cyber security must have ability to protect underlying infrastructure of networking from misuse, malfunction or unauthorized access. So that a secure and safe platform can be created for all computer systems (Piplai, et al., 2019).
- Problem solving: cyber security officer must posse’s skill of problem solving as hackers always try to infiltrate systems with new techniques and an analyst must have solutions of these problems.
- Policies of information security: these are some rules that formed by a particular organization to ensure all networks and users of IT structure within company can stay secured.
- Firewall administration: firewall can be defined as a device for network security which control network traffic and decide which traffic to be allowed or which is to be rejected on based of defined rules for network security.
- Network protocols: network protocols can be defined as policies or standards made by rules, formats, procedures, that define communication in between devices over any network.
- Routers, switches, hubs: Hubs can be defined as dumb devices that have ability to pass one to other connections. Switches can be defined as semi intelligent device that knows which device has which connection, routers are very intelligent and can perform many tasks.
- Process improvement: it can be defined as a task of identifying, analysing and after that improving business processes which were not that good previously. This must be done for optimization of organization and to reach to new quality standards.
Curriculum Vitae
ABC
Cyber Security Analyst
Phone: (0123) 456789 | XXX@gmail.com | Website: demo.com
SUMMARY
Verified Cyber Security Analyst having more than 6 years of expertise in system security, intelligence, security operations and cyber-crimes investigator. Skilled in risk assessment and handling, Risk Management Framework (RMF), vulnerabilities handling, Assessment as well as Authorization. Can efficiently interact with a number of different individuals, agencies, interests and constituencies.
CORE COMPETENCIES
Network Administration of TCP/IP, Penetration Testing, Antivirus, Antimalware, Vulnerability Scanning, Network Security, Framework Assessment, Snort and Nessus Risk Management, POAM Management, Authorization and Authentication, NIST, CSAM, FISMA, Firewall, FIPS Security Control Assessment and prevention Protocols/ Intrusion Detection, Mainframe, Windows, Linux and Unix Operating Systems, Packet Analysis Tools and Network Protocols.
PROFESSIONAL EXPERIENCE
Cyber Security Analyst
Lookout June 2013 – Present
Key Deliverables:
- Interviewing system admins and other shareholders in support of the AA process to assist in generating personalized reports and/or artefacts.
- Identifying security checks and building a compliance matrix for monitoring.
- Apply adequate Federal Information System Cyber Management Regulation focused on NIST 800-37, analyse risks and weaknesses based on realistic studies.
- Supports us by protective cyberspace operations (DCO) with cyber guidance and central command (Centcom).
- Performing as the Cyber Protection Team Reduction Squad (CPT) information-security analyst within the network security divisions.
- Protects essential assets and main services inside the global knowledge system agency for security.
- Providing protection assistance to FISMA and Nist process information system security officers (Isso), and touch level.
- Implement security assessment as well as authorization environments like network protection categorization, safety and contingency plan creation, security testing & review, device accreditation, and ongoing tracking.
System Support Engineer
Crowdstrike January 2012 – May 2013
Key Deliverables:
- Undertakes all-source information review of the strengths and risks of adversarial cyberspace by investigation and study.
- Researching, preparing, deploying, configuring, troubleshooting, updating and improving operating systems.
- Diagnose the problem and fix issues with equipment, applications, and networking including device control and synchronization of devices.
- Computer equipment and peripherals mounted, programmed, and modified to also include the network card, scanners, modems, and add-in panels.
- Imaged machines and network administration tools utilized for ticketing services support desk.
- Addressed remedial steps to prevent intrusion identification and destruction of viruses, and malware.
- Helping consumers define the problems through the use of the information base.
- Provide technical assistance of the information network to a broad variety of clients in industrial national security settings.
- Provide technical assistance to a broad variety of users in the industrial information security field via the computer network.
- Use predictive technology to track network irregularities and harmful communication.
- Use predictive technology to track network irregularities and harmful communication.
- Help for the deployment and troubleshooting of desktop and portable devices on Linux, macs, android, Windows computers, and iOS handheld apps; problem / incident reporting, and problem / scaling.
- Using advanced analytics discover anomalies in networks and malicious traffic.
EDUCATION
Master of Science May 2016(Malborne University, School of Graduate &
Professional Studies , MD)
References
Narayanan, S. N., Ganesan, A., Joshi, K., Oates, T., Joshi, A., & Finin, T. (2018, October). Early detection of cybersecurity threats using collaborative cognition. In 2018 IEEE 4th international conference on collaboration and internet computing (CIC) (pp. 354-363). IEEE.
Piplai, A., Mittal, S., Joshi, A., Finin, T., Holt, J., & Zak, R. (2019). Creating cybersecurity knowledge graphs from malware after action reports.
Palmer, C., Angelelli, L. A., Linton, J., Singh, H., & Muresan, M. (2016, September). Cognitive Cyber Security Assistants—Computationally Deriving Cyber Intelligence and Course of Actions. In 2016 AAAI Fall Symposium Series.
Washington, T. (2017). Critical Skill Job–Cyber Security Analyst. Savannah River Site (SRS), Aiken, SC (United States).
Individual Analytic Report
Executive Summary
Data is an essential asset which helps in creating the competitive advantages over organization. Data Analytics helps organization develops operational efficiency, drive new income, & increase competitive advantage. In this report, how data analytics provides business to users or organizations has been discussed by choosing the SPSS tool. SPSS is termed as Statistical package for the Social Sciences which are use to solve difficult statistical data analysis. SPSS issued by market researchers, health researchers, marketing organizations, & many more for analysing the data. In this report two types of data analytics can be discussed i.e., predictive & prescriptive, Why SPSS tool in data analytics will be chosen & why it is used & the improvements to the data analytics to user or organization by using SPSS tool has been further discussed in assignment. For improving the business growth of any organization, it needs to collect related information.
Research Question
How can data analytics provide (business) value to users &/or organisations?
Introduction
The report includes the details about the data analytics done in the business. The report includes the detail about the importance of the data analytics to the users & the organisation. The software used in this report for the data analytics is the SPSS solutions. The SPSS solutions are the software package that is used for the interactive statistical analysis that is done in the business or organisation. The current name of the SPSS tool is the IBM SPSS Statics. This tool is used by the large number of the organisation for the statistical analysis in social science. The SPSS statistics focuses on simplifying the programming by including the internal file structure, data processing, data type etc. this tools used by the various researchers in making the statistical analysis of the data. The programs offered by the SPSS tool are statistics programme, modeller programme, visualisation designer & text analytics for survey programs.
Importance of data analytics
Data analytics is important to the business & the users. Data analytics is needed in the business to consumer applications (Devi et. al., 2013). The organisation collects the data from the consumers & then this data is gathered & categorised after this the analysis is done. The data analytics will help the business to grow. Therefore, it can be said that there is certain factor that can define the importance of data analytics in the business such as:
Analysis of business value chain
The data analytics helps the business to analyse the ways in which the existing information can be used to help the business in finding the way to the success.
Industry knowledge
The data analytics helps the business to gain the knowledge about the industry. In this the business can get the knowledge about the ways they can adopt to succeed in future (Chen et. al., 2012). It also helps to analyse the economy that is avail bale with the business.
Seeing the opportunities
The data analytics helps the business in analysing the data that can help in creating the opportunities for the business. It is said to be the way of unlocking the various options for the business.
It benefits the users as they can get the collected data in the systematic form that can help them in making the decision easily. Therefore, it can have said that the data analytics benefits both the users & the organisations & provides various facilities to them.

(Source: digitalvidya.com)
Executives of chosen data Set- Predictive & Prescriptive
Predictive analytics
Predictive analytics help to link data to successful action by representation dependable conclusions about current events & situations (Arkkelin, 2014). This helps in organization to practical in cutting cost, reducing risk & increasing profitability, optimizing their business & driving latest form of business.
The SPSS predictive analytics software used for:
- Transform data into predictive approaching to direct frontline choices & interactions.
- Predict what consumers want & will do further to enhance profitability & retention (Ayhan, et. al., 2013).
- Increases efficiency of the individual, process & resources.
- Identify & avoid threats & frauds before they influence the association.
- Determine social media effect of the products, services & marketing campaign.
- Execute statistical analysis as well as regression analysis, cluster analysis & correlation analysis (Agudo-Peregrina, et. al., 2014).

(Source: IBM, 2019)
Prescriptive analytics

(Source: DSC, 2019)
Prescriptive analysis can used to find out the best solution or results with all choices, given the recognized parameters (Vajjhala, et. al., 2015). When combined the predictive analytics, the prescriptive analytics can recommend result option for how to take benefit of future prospect or moderate upcoming risks. This analytics gives vast value to planners & decision makers .The main reason of the prescriptive analytics is not still widely used in difficult planning processes is that frequently these processes are exceptional to the organization. The accessible SPSS tools that previously offer superior planning together with prescriptive analytics don’t manage well among these business particulars (Keahey, 2013). It improves operations, reduces risk & mange resources efficiently.

Fig: Afghanistan Marital Status for men and women
Why it is used & why it is chosen or laid out in fashion
SPSS was chosen due to its ubiquity within equally scholarly & business circles, building it the most generally used collection of its type. SPSS is similarly flexible packages that permit a wide variety of kinds of investigation, information change, & types of give up in short; it will further than satisfactorily fill their requirements (Sun, et. al., 2014). SPSS tool is utilized for both subjective & quantitative investigation can be examined by the product along these lines making the specialists work simpler. In this way, why SPSS is significant in information examination can’t be undermined since it has altered the information investigation process.
To condense what they have canvassed in this section, they will advance throughout accompanying strides as you make & execute a SPSS program:
- Access SPSS for Windows from PC hard drive or from system (LAN)
- Create an information record in SPSS Data Editor or SPSS Syntax Editor
- Save information record utilizing suitable document expansion (.SAV or .SPS)
- Specify an investigation to be kept running on information document (e.g., Frequencies)
- View consequences of an examination in SPSS Viewer Window
- Save yield record in this Viewer Window utilizing the SPO document amplification (Schoenherr & Speier‐Pero, 2015).
Practical Approach

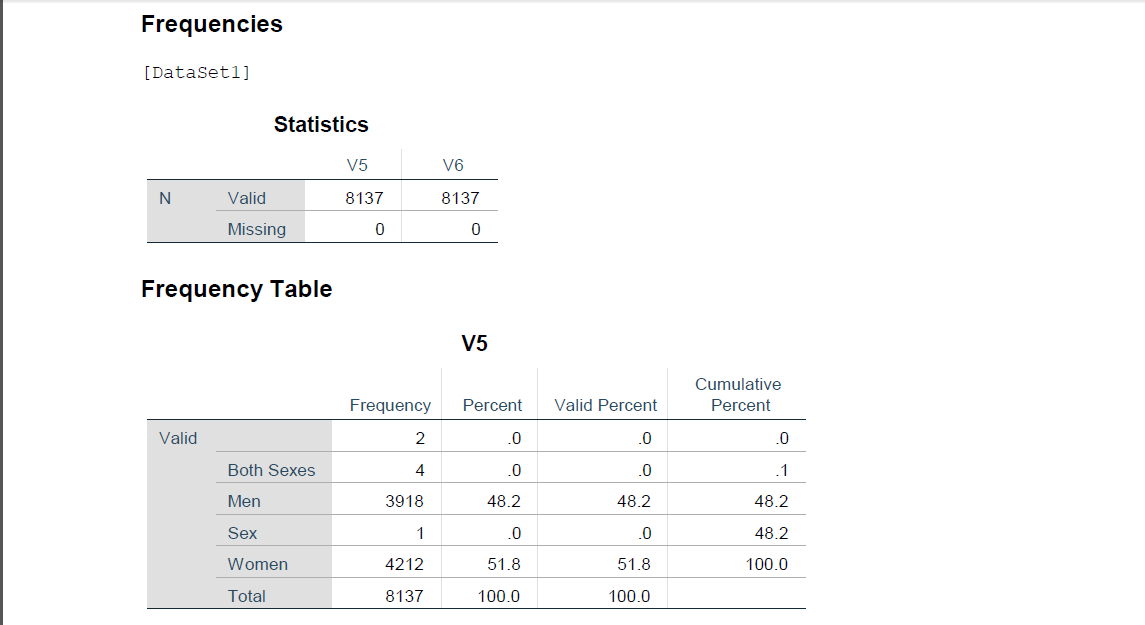





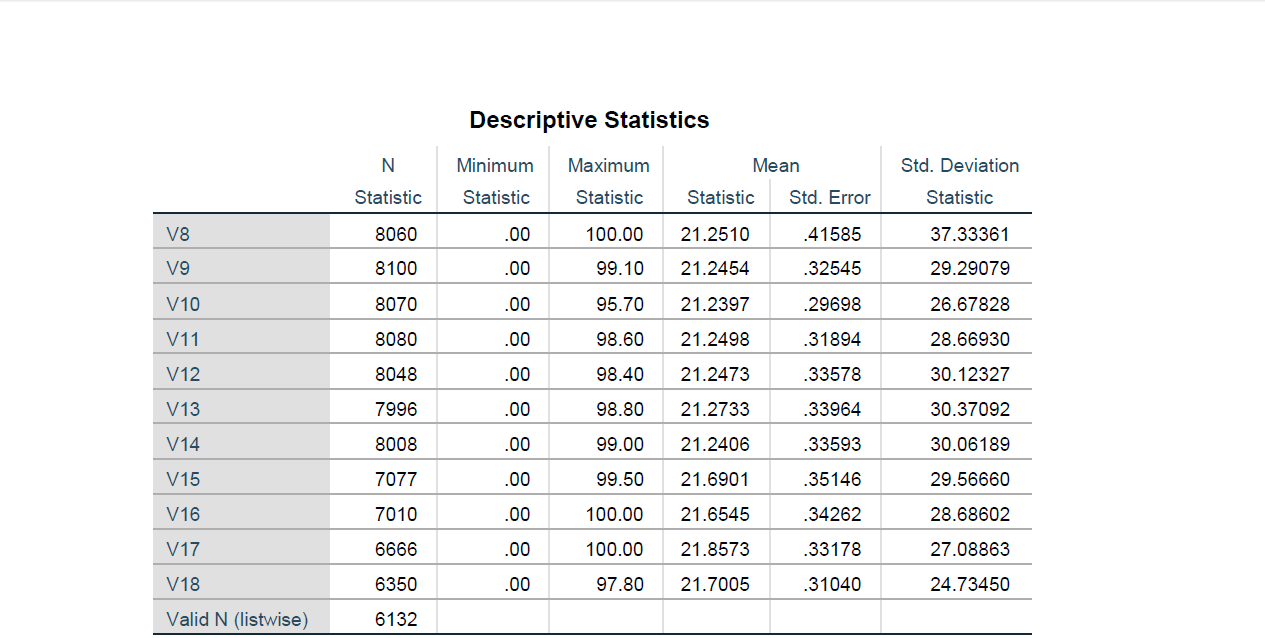


Improve the operations
The CEO wants to improve the operations, the use of the tool SPSS solutions can help to improve or enhance the sale & operations of the company. The CEO should use the predictive analysis of the tool so that can help in predicting the outcomes, make smarter decisions & getting the better results for the company. The improvement can be made by the company by saving the money through the predictive analysis. Therefore, it can be said that the predictive analysis can help the business in saving the money (Duan & Xiong, 2015). The operation can be improved by avoiding the costly problems that can occur in the operations. This can be done as the SPSS tool can help in predicting the operating characteristics of the business cost effectively & accurately that can help in analysing the factors that can generate the downtime or the benefits to the business. Another through which the operations can be improved by the CEO using this software, as the predictive analysis can impact the profitability & the competitiveness of the organisation. The predictive analysis through this tool can help the business in to turn the vast amount of structured & unstructured data into actionable one. Therefore, through this it can be seen that there are various ways that can be used by the business to improve the operations & increase the sales of the business through the use of the SPSS solution tool.
Conclusion
Through this report it can be concluded that the tool that has been used for the data analytics is the SPSS solutions. It is the best tool as it can help to improve or enhance the sale & operations of the company. Data analytics is important to the business & the users. The data analytics helps the business to analyse the ways in which the existing information can be used to help the business in finding the way to the success. The report includes the details about the data analytics done in the business. The report includes the detail about the importance of the data analytics to the users & the organisation.
References
- Agudo-Peregrina, Á. F., Iglesias-Pradas, S., Conde-González, M. Á., & Hernández-García, Á. (2014). Can we predict success from log data in VLEs? Classification of interactions for learning analytics and their relation with performance in VLE-supported F2F and online learning. Computers in human behavior, 31, 542550. Retrieved from: https://www.sciencedirect.com/science/article/pii/S074756321300188X
- Arkkelin, D. (2014). Using SPSS to understand research and data analysis. Retrieved from: https://scholar.valpo.edu/cgi/viewcontent.cgi?article=1000&context=psych_oer
- Ayhan, S., Pesce, J., Comitz, P., Sweet, D., Bliesner, S., & Gerberick, G. (2013, April). Predictive analytics with aviation big data. In 2013 Integrated Communications, Navigation and Surveillance Conference (ICNS) (pp.113). IEEE. Retrieved from: https://ieeexplore.ieee.org/abstract/document/6548556
- Chen, H., Chiang, R. H., & Storey, V. C. (2012). Business intelligence and analytics: From big data to big impact. MIS quarterly, 36(4). Retrieved from: https://pdfs.semanticscholar.org/f5fe/b79e04b2e7b61d17a6df79a44faf358e60cd.pdf%3E.
- Devi, B., Rao, K., Setty, S., & Rao, M. (2013). Disaster prediction system using IBM SPSS data mining tool. International Journal of Engineering Trends and Technology (IJETT), 4, 33523357. Retrieved from: https://www.statwks.com/wp content/uploads/2019/03/Disaster-Prediction-System-Using-IBM-SPSS.pdf
- Digitalvidya, (2019). About us. [Online] Digitalvidya. Available at: https://www.digitalvidya.com/wp-content/uploads/2017/04/Data-Science.png . [Accessed: 17 September 2019].
- DSC, (2019).Welcome to data science central. [Online] DSC. Available at: https://www.google.com/url?sa=i&source=images&cd=&cad=rja&uact=8&ved=2ahUKEwiy7fKQ7tfkAhWDdn0KHfOKBnIQjhx6BAgBEAI&url=https%3A%2F%2Fwww.datasciencecentral.com%2Fprofiles%2Fblogs%2Fprescriptiveanalytics&psig=AOvVaw3fKTPyYBGqKs43SuwBVZH4&ust=1568809754870048.[Accessed: 17 September 2019].
- Duan, L., & Xiong, Y. (2015). Big data analytics and business analytics. Journal of Management Analytics, 2(1), 1-21. Retrieved from: https://vivomente.com/wp-content/uploads/2016/04/big-data-analytics-white-paper.pdf
- IBM, (2019).About us. [Online] IBM. Available at: https://www.google.com/url?sa=i&source=images&cd=&cad=rja&uact=8&ved=2ahUKEwiVnr27dfkAhUJ7XMBHeRoAiUQjhx6BAgBEAI&url=https%3A%2F%2Fwww.ibm.com%2Fdeveloperworks%2Fcommunity%2Fblogs%2Fibmbi capabilities%2Fentry%2Fpredictive_analytics_with_ibm_spss_basic_q_as&psig=AOvVaw3kjIHcJcM0v5ZMt9I6yyWh&ust=1568809598168726. [Accessed: 17 September 2019].
- Keahey, T. A. (2013). Using visualization to understand big data. IBM Business Analytics Advanced Visualisation. Retrieved from: https://dataconomy.com/wpcontent/uploads/2014/06/IBM-WP_Using-vis-to-understand-big-data.pdf
- Schoenherr, T., & Speier‐Pero, C. (2015). Data science, predictive analytics, and big data in supply chain management: Current state and future potential. Journal of Business Logistics, 36(1), 120132. Retrieved from: https://onlinelibrary.wiley.com/doi/abs/10.1111/jbl.12082
- Sun, N., Morris, J. G., Xu, J., Zhu, X., & Xie, M. (2014). iCARE: A framework for big data-based banking customer analytics. IBM Journal of Research and Development, 58(5/6), 4-1. Retrieved from: https://ieeexplore.ieee.org/abstract/document/6964895
- Vajjhala, N. R., Strang, K. D., & Sun, Z. (2015, August). Statistical modeling and visualizing open big data using a terrorism case study. In 2015 3rd International Conference on Future Internet of Things and Cloud (pp.489496). IEEE. Retrieved from: https://ieeexplore.ieee.org/abstract/document/7300857
Introduction
This report will be based on a case study which determines about hairdressing chain. This study is based on Cut Short Salon which implements some new feature in their salon. According to the study, these features increase profitability. It addresses some recommendation which improves these new features and increases the rate of customer. It will address the new point which needs to be focused by the organisation and enhances the brand’s image of the organisation at the international level as well. Suggestion describes those concepts which need to be developed in the habit of the salon. Development and improvement are required for every organisation to grow in the same industry. This report will say that the salon needs to implement technology and the new technique which is useful for increases its brand image of a specific. Image is not enough. The salon must prove that its management and service is an exact what they promote in the market. Sponsorship will also help them to grow.
Question 1
In the field of salon service, the Cut Short started its works in the hair cutting and styling service. This organisation provides its hair styling services to its customer who would be booking its appointment from the online services. In this field, there are various organisations which provide efficient service to its customer. According to the report, the customer gets the advantage of service from the Cut Short. They save up to 15 minutes of each customer by providing the new advanced feature in its services. The recent adoption of new facility saves lots of time for each customer who visits the salon. When a customer visits the salon, the choosing styling takes time from the available services and the payment methods also took more time. These processes are very time consuming for every customer (Catherine, 2016). Cut Short implement some features which increase the profitability and minimize the time consuming by the customer. The implementation is as follows:
- a) Pre-booking appointment through online service (website) of the organisation –customer can select the service like restyle, blow wave, trim etc. with date and time.
- b) When customer completed appointment or pre-booking- the payment also is made online from the credit card or PayPal.
- c) Cut short encourages its customer for pre-booking, online payment by offering a 10% discount.
d)If the customer does not reach on their appointment time, they will be penalised from extra charge.
These features add by the Cut Short Salon which increases its profitability and optimizes the time resource in an efficient manner. The customer appreciated these feature because it reduces the complexity of booking, minimises the time for payment queue and significant use is to save the time for choosing a hair styling method (Dean, 2012).
Recommendations for the Cut Short Salon are:
Brand Awareness
It is a significant factor for any organisation that increases the profitability of the business. Cut Short Salon needs to increase its brand awareness in the local public. It increases by the rate of customer who visits the salon and at least tries once that particular service. The techniques required for brand awareness are brand ambassador, advertisement in print media by offering unique features or discount offers from another salon. Hire a celebrity who promotes the specific brand and performs advertisement on social media and television.
Nowadays, social media is one of the best platforms for the promotion. If a celebrity promotes a specific organization or some brand, people automatically attract by and try at least once. The process of brand awareness requires lots of time, and more effort but organisation surely achieves the particular objects of the organization. Salon draws the attraction by providing unique hair styling features in fewer amounts, by providing combo offers or the special day in which they must offer a 50% discount to the customer (Engineering Business Journal, 2015).
According to the case study that Cut Short Salon provides pre-booking service on its website. If a celebrity shares the particular link of their website by which customer can easily access and take advantage of its service. Customer take services and they impressed from the salon service. It has the vast possibility that customer will become a regular customer. These strategies will be helpful to attract the customer.
Pamphlet will be distributed with the newspaper in the local areas. Fashion magazines include some part of the salon which says about newly updated services of the Cut Short Salon. There are some other alternatives which enhance brand awareness among people, i.e. Salon must collaborate with the modelling association, film industry. These associations are a very significant resource for brand awareness, and it is the primary tools which increase the growth of Salon. If the quality of work is more appropriate according to the expectation, respective Salon grows its brand in international based (Lewis, 2012).
Salon’s Administration
As per the case study, salon improves various features and updated its service according to the demand of time, but Salon needs to be organized its administration as per its services. The customer expects to prefer those salons which give respect and treat well in the accordance of behaviour, attitude and the preference in the service. When customers visit the salon, first visit reception window and book its seat or inform about its pre-booking service about its respective function. It is the duty of receptionist that they respectfully welcome the customer and listen carefully about the service customer. If there is a massive queue maintain or manage accordingly that every customer will be satisfied with their preference level (Pocol, 2012).
After that, the customer will be seated for offering their services. Space must be hygienic, the use of the product should be high quality or original, the use of clothes or towel should be clean, the administration should take care of unwanted noise etc. These features will provide an initial level of relaxation and satisfaction to the customer.
Further, all these services, customer move towards the payment gateway if they already paid by online means that they avoid this step. Those customers who not paid online that give pay by cash, PayPal, credit card, debit card etc.
Employees of the respective salon must keep their attitude low in front of the customer and listen to the issues of the customer and gives them to the service according to their expectation (Soltani, 2016).
Innovation (Mobile Application)
This era belongs to the technology means, Cut Short Salon developed its website and offered the various feature on it. But it requires one further step towards technology. This Salon needs to improve its mobile application which enhances the level of participation towards the salon. Mobile Application is easy too, and notification will recommend the customer for special service.
The salon must be updated according to the hair styling options with the product because now people like to use the branded product. It increases the image in front of the customer that respective salon use branded product which surely brings improvement on their scalp of hair (Tsai,J.et.al., 2012).
In traditional time people goes only on some special event or in monthly but now the time will change the mind of people. Mobile Application notifies about the unique offer and the reviews of customers as well.
In home page- Screen will be divided in some section like hair. Special part has subparts and like hail colouring, hair styling, hair cutting, hair straightening etc.
These sections will tell about the service and customer can access the information regarding particular service. This subpart information contains the product used for the service, specialist name, charges and charge will pay at the time of pre-booking. This method is taking less time and customer will get a notification if their pre-booking will be confirmed. Cut Short Salon get more benefit if they get the offer of home service because it will be charged more according to the service at the salon.
This service will be available when the salon develops its mobile application and enhance technology. Pre-booking of service will be cancelled or postponed. This facility should be available at that app. If somebody cancelled its appointment, the amount would be deduced so that unwanted customer will not increase the traffic at the server (Wei, 2016).
This service shows that how many salons involved in the technology world and its make reliable towards the function of the salon. It will enhance the level of contribution from the sponsor products.
Beauty product and hair styling product companies are collaborating with those salons that make good its image in between the market.
Question 2
The unique suggestion which helps to improves the business service or operation offerings are as follows:
Use reliable products
The salon must focus on its regular contacts like they should always trust on reliable and original. The reliable hair product may be expensive, but the salon includes its habit that they never compromise with the product quality if the constraint is price, time or store. Cut Short Salon must highlight those things which might be attracted to the number of customers. The highlighted factor may be a reliable product and trustworthy. If salon undergoes in the sponsorship, they must be used by them only after appreciating by staff or salon individual. After this, the salon used or apply customer. Mostly, salon used various which give more fund for their sponsorship. If Cut Short Salon wants to grow at the international level, its essential requirement is to sponsor a global beauty product. Now a day people like to prefer international product because it believes that international product is more reliable due to its brand awareness among people. It enhances the rate of performance and customer rate. Salon proves that these products require the best service due to the human effort as well because every product demands specific effort and style. It will be determined when the salon staffs give their best and push their effort according to the demand for a particular product. Customer is curious about international services like hair spa, hair straightening etc. The salon should take a step towards that which maximizes the profitability and increase images in the market (Lewis, 2012).
Implementation of new service
New service will increase the excitement in the existing customer, and it attracts a new customer. The salon should be updated with the service which is recently implemented in the local market or international market. This strategy will complete the demand of customer and fulfils their expectation. People get aware about new service from social media, movies and serials. After watching videos and read about them customers want to implement on them also. But they want to give this chance to the experience personality or the reliable salon which can them easily trust and accept the new implementation. For example, a hair spa treatment is only for models or actress because of little bit expensive, and it requires good quality of the product. So just actors and models use this treatment, but nowadays it is entirely reasonable because salon uses technologies and gives hair spa according to the nature of hair and scalp. These strategies made profitable, so that salon starts implementation according to the market demand. Customer appreciates this theory and contributes their best favour. So, Cut Short Salon moves on this direction and offer new service to its customer. By this, salon increases its brand image because when it is ready to implement, they should advertisement in social media and give offers to the customer in their first service. It increases profitability, and it provides unique space in the same platform (Wei, 2016).
Conclusion
This report concludes the recommendation and suggestion of hairdressing chain. It was based on the case study in which a Cut Short Salon add some new exciting features which increase their profitability like pre-booking services, online payment through website reduce the wastage of time. It is the strategy which efficiently optimises the resource. Recommendation proves that salon needs to improve its existing service in a particular way and suggestion offers those strategies which enhance the rate of profitability with the traffic of new customer. This study concludes that salon is also a profitability sector because it increases or grows according to the time.
References
Catherine,B.,(2016).Redundant technology in the salon. Professional Beauty,pp. 118-119
Dean,D,H., (2012). Gender ethnic identity and patronage likelihood for a unisex hair salon.Young Consumers. Vol.13(2).pp. 124-135
Engineering Business Journal., (2015). Salon Allure Trade Show Evolves To Become “Hammock” With New Categories, Technology And Design. Engineering Business Journal.
Lewis, J. (2012). Festive party season the ideal time to promote your salon. Hairdressers Journal International.p. 5.
Pocol, A. G. (2012). Modern tools for sales promotion–online promotions (Report). The Proceedings of the International Conference, Marketing – from Information to Decision. Issue 5.p.380(16).
Soltani, Z. &Navimipour, N. J. (2016). Customer relationship management mechanisms: A systematic review of the state of the art literature and recommendations for future research. Computers in Human Behavior. Vol.61. pp.667-688
Tsai,J.et.al., (2012). The Effective and Quality Approach to Reduce the Turnover Rate for Hair Salon Industry.International Journal of Sociotechnology and Knowledge Development.Vol. 4(4). Pp. 44-57.
Wei, J. T. Lee, M. C. &Chen, H. K. Wu, H. H. (2016). Customer relationship management in the hairdressing industry: An application of data mining techniques. Expert Systems With Applications. Vol. 40(18). Pp.7513-7518.