Post 2
ACS Code of ethics is the element of ACS constitution. As the member of this constitution I must advance and uphold the effectiveness, dignity and honour of being professional. As a good citizen I must adhere the following society values –
- Honesty
- Competence
- Professionalism
- Primacy of public interest
- Professional development
- Increment in quality life (ACS, 2020).
These are the components of ACS code of ethics. Now, to solve the ethical dilemma that we discussed above such as deontology, utilitarianism, social contract theory and character based ethical theory, I would suggest the IT professionals, surgeons and patients also to do act in accordance with the ACS codes of ethics. To become a good citizen of Australia every individual must adhere the principles or components discussed above.
In honesty, the surgeon and IT professionals should be honest in terms of representing their knowledge, skills, products and services (ACS, 2020).
With this ACs value, the surgeon and IT professionals would be able to distinguish between their personal opinions and professional opinions.
In Competence, the surgeon and IT professional must apply their work diligently and competently for their stakeholders (patients).
With this ACS value, the surgeon and IT professionals will accept their responsibility regarding their professional activity. This will not permit both of them to misrepresent their knowledge and skills (Users, 2020).
In professionalism, as a professional surgeon and IT professional they must increase the integrity and they should respect their patients.
This ACS value will help in continuous upgrade of knowledge and skills of surgeon and IT professional. This will also tell both that whether their work is affecting their profession and their relationships with others (Teaching, 2020).
In Primacy of public interest, in this component of ACS code of ethics all the professionals must place public’s interest over their own personal, sectional and business interests.
This value helps in identifying those individuals who are impacted by the work of surgeon and IT professional. This will help in identifying any type of conflict within the profession and the professional activity.
In Professional development, the surgeons and professionals have to increase their own professional development and of their staff and colleagues as well.
This ACS value will help surgeon and IT professionals to take a calm, informed, knowledgeable and objective stand on their professional work. This will also help in endeavour o expand knowledge of public and their understanding on ICT.
In Increment in quality life, the surgeon and the IT professionals are responsible for struggling for the quality life which does not affect the others by your work (ACS, 2020).
With this ACS value the surgeon and It professionals would be able to promote and protect the health and safety of those individuals who are affected by your professional activity. This will be helpful in getting personal satisfaction, control over those affected and competence.
When it comes to become a good citizen every person must adhere these principles of ACS code of ethics. This leads to peace, and good application of the knowledge and learning.
In situation of such dilemma between different values, Primacy of public interest obtains preference over other values. These ACS codes of conduct basically aim at someone as a practitioner individually and these codes of conduct will then be guidelines for the acceptable professional conduct. These guidelines will be applicable to the members of the ACS who are the surgeon and IT professional given in the case study. These codes of conduct will be helpful in dealing with such kind of dilemmas. The ACS values discussed above will be helpful in resolving the dilemmas (Teaching, 2020).
References
- ACS, (2020). About ACS CODE OF ETHICS. Available at – https://www.acs.org.au/content/dam/acs/acs-documents/Code-of-Ethics.pdf. [Accessed on – 19 April 2020].
- Wood-Black, F., & REM, M. (2016, August). What’s in a Code of Conduct?. In ABSTRACTS OF PAPERS OF THE AMERICAN CHEMICAL SOCIETY (Vol. 252). 1155 16TH ST, NW, WASHINGTON, DC 20036 USA: AMER CHEMICAL SOC.
- Teaching, (2020). About Australian Computer Society Code of Ethics. Teaching. Available at – http://teaching.csse.uwa.edu.au/units/CITS3200/ethics/acs-ethics.htm. [Accessed on – 20 April 2020].
- Users, (2020). About Australian Computer Society CODE OF ETHICS. Users. Available at http://users.ece.utexas.edu/~perry/education/SE-Intro/ACS-COE.pdf. [Accessed on – 20 April 2020].
Learning area: Software Testing
Introduction
A software system is a basic necessity for every industry active across the globe. The primary use of the software system is to operate routine activities and accomplish their tasks with precision. However, before including any software system, its evaluation is essential to ensure the software runs with Zero flaws. A minor negligence in software evaluation can impact organizational growth and branding.
To evaluate the effectiveness of any software system, standards are defined. Standards are the methodology that is used for identification, analysis, validation, and quality check of any software. The report presented hereby is based on Existing Formal Standards and BCS Proto-standards, proposed by B. A. Wichmann. Many other researchers have proposed other software testing standards as well, but here we have discussed one of the two standards proposed by B. A. Wichmann.
Responses to questions
- What is the standard name?
ANSI/IEEE STD 829 Software Testing Documentation
- Who holds the copyright for the standard?
IEEE (Institute of Electrical and Electronics Engineers)
- Amongst the acknowledged contributors to the document, which universities were involved (if any)?
NA
- What is the scope or intent of the standard?
The ANSI/IEEE Standard 829 applies to all software-based systems that are acquired, maintained, operated, or being developed as well. During the testing procedures, it’s crucial to acknowledge the software interaction with every system part and its outcomes. This software testing standard gives you descriptive information about completeness, consistency, accuracy, and testability of the software system alongside delivering detailed information about software correctness.
Sole purpose of using the IEEE 829 Software Testing Standard is to set up a common framework for all Software Life Cycle processes. The common SLC processes include acquisition, supply, development, operation, and maintenance processes. Under this IEEE STD 829 standard, the test processes will involve defining the test tasks, calculating required inputs & outputs.
- What are key terms and understandings needed for the standard to be understood and applied?
IEEE: IEEE is the acronym of Institute of Electrical and Electronics Engineers that is an association for Electronic & Electrical engineering. It is headquartered in New York, whereas its operational center is in Piscataway (New Jersey). In 1963 IEEE came into existence after the amalgamation of the American Institute of Electrical Engineers and the Institute of Radio Engineers.
Informative: This term is used many times in the entire report. The term explains the information associated with every single Standard applied to the software system for testing purposes. It is used for additional information and guidance purpose (Basso & DeBlasio, 2012).
CIF (Common Industry Format): This is a standard format accepted by the industry to acknowledge the testing results and outcomes of the software testing.
Component Testing: Software is made of multiple modules/components. So, it’s essential to ensure every component is working correctly and delivering the desired results. Component Testing is the term used for testing every single software component associated with the software system (Cadar & Sen, 2013).
Quality Assurance: Quality Assurance is the format to avoid mistakes in the software system and overcome problems that cause issues in delivering appropriate services to the industries/customers.
Standards: This entire report is based on the Standard that we are using for Software system testing. Software testing requires different parameters and methodologies to evaluate its effectiveness and quality. Standards are that methodology that tests the software on various aspects and evaluates its effectiveness (Sawant, et al., 2012).
- In your own words, what does application of the standard result in? Or, in other words, what does the standard do?
The sole purpose of executing this IEEE Standard 829 is to evaluate the software correctness and ensure the software system is fully functional without having any flaws. This standard includes verification, demonstration, analysis, inspection, and validation of the software (Khersonsky & Sulligoi, 2015).
Moreover, it will also help us acknowledge whether the software system is legit for use by industries or not.
- Finally, what specific relevance to software testing is the standard?
The standard is used for software testing provides a low to high integrity level that enables an easy way to acknowledge the software quality as well as its importance (Muccini, et al., 2012). In every integrity level, minimum testing tasks are assigned that are based on the task intensity. The selection of the test document is another smart approach to provide optimal results.
Comparison between research paper and the chosen standard
Starting from the research paper, for software testing, the issue was considered in a narrow sense. It means, for initial testing, the software code is executed to acknowledge the proper functioning of code, flawlessly (Yu, et al., 2013). This way, we get the initial checks and testing outcomes. The entire research paper concentrates on component testing. In majority, research is targeted on the functioning of different aspects of the software. That includes data flow features. At each level, the test is executed to conclude the outcome, often known as test effectively. At last, the effectiveness of our testing is entirely based on three primary factors:
- Level of testing performed;
- Test strategy selected; and
- Test coverage to be achieved.
Now, coming to the IEEE STD 829, we used a common framework for test processes to test through all software life cycle processes. Comparing the research paper with the Standard we proposed, it was found that the IEEE Standard 829 passes the three primary parameters and gives positive results at the end (Schuh, et al., 2013). However, the outcome in the IEEE 829 testing Standard was entirely based on accuracy, testability, and completeness of the tasks. Above all, this testing Standard applies to all software systems providing a broad scope for the industries and organizations to get assured results.
Conclusion
The report presented hereby includes one standard that is considered on the software systems to get feasible results. The entire information associated with the IEEE STD 829 has been elaborated by answering a few questions related to the Testing Standard. Furthermore, the crisp comparison between Research paper and Chosen Standard has also included in this report. Followed by question & answers, a summary of entire report findings is also included to deliver you the whole process of testing along with the outcomes.
References
- Basso, T., & DeBlasio, R. (2012). IEEE smart grid series of standards IEEE 2030 (interoperability) and IEEE 1547 (interconnection) status (No. NREL/CP-5500-53028). National Renewable Energy Lab.(NREL), Golden, CO (United States).
- Cadar, C., & Sen, K. (2013). Symbolic execution for software testing: three decades later. Communications of the ACM, 56(2), 82-90.
- Khersonsky, Y., & Sulligoi, G. (2015). Standards for Ships and Oil Platforms: A Review of the Latest from the IEEE and IEC. IEEE Industry Applications Magazine, 22(1), 20-27.
- Muccini, H., Di Francesco, A., & Esposito, P. (2012, June). Software testing of mobile applications: Challenges and future research directions. In 2012 7th International Workshop on Automation of Software Test (AST) (pp. 29-35). IEEE.
- Sawant, A. A., Bari, P. H., & Chawan, P. M. (2012). Software testing techniques and strategies. International Journal of Engineering Research and Applications (IJERA), 2(3), 980-986.
- Schuh, M., Sheppard, J., Strasser, S., Angryk, R., & Izurieta, C. (2013). An IEEE standards-based visualization tool for knowledge discovery in maintenance event sequences. IEEE Aerospace and Electronic Systems Magazine, 28(7), 30-39.
- Yu, L., Lei, Y., Kacker, R. N., & Kuhn, D. R. (2013, March). Acts: A combinatorial test generation tool. In 2013 IEEE Sixth International Conference on Software Testing, Verification and Validation (pp. 370-375). IEEE.
Requirements analysis and design
Use cases of the takeaway system with requirements
Use case name: See the menu, place the order and initiate the payment
Actors
Ana
Other managers and cooks
Customers
Many display system
Order management system
Payment gateway and billing system
Triggers
The owner wants to explain and display all the contents of the menu, and the special packages. The customers should be able to select the packages, see the costs, and should be able to pay the cost of the selected dishes.
Preconditions
The users and customers have selected the food items and also purchased using the payment gateway.
Postconditions
- The system can be used to place the order.
- Users can know about their selected and ordered packages.
- An estimation of the time to complete the order is also can be displayed.
Normal Flow
- Ana will open the system.
- She will be able to see the available food dishes, special packages and other offers with their prices.
- She will select the dishes, and confirm their order.
- Ana will be able to see the details of the payment amounts that were received from Pizzas and Pasta.
- Ana will be able to see the details of the amount of the Pizzas and Pasta that were sold at that session.
UML diagrams
A use case diagram for processing and order
Development of the code
Functionality to process the ordering
Following points are described as the functionality of processing the orders:
Database Stock
It is a monthly update regarding the stock position. It will help Ana to know about the amount of the raw material as well as the prepared food that can be added in the packages too. This function will make the program efficient as it is one of the basic necessity to develop the program.
Sell-in Plan
It is an operation target that is used to aim the S&OP divisions which are related to the volume and amount of the order. This will be required to know the ordering quantity and manage the amount of food.
Recommendation of the PO
It is a document that contains the recommendation regarding the stock that is to be build up to manage the sell history and amounts of the sold food items. It has the introduction of the products and service of the system and business, the recommended sr=trategy to distribute and manage the order processing technique, the sales history. It is beneficial for the sales and operations department to get an idea about the targets and goals.
Confirmation of PO
The PO confirmation is an ordering document, which is also used for the communication between the distributor, sales department, and operation department. The number of orders and the amount of the product that is ordered are accessed and managed by this function.
The sales order
The sales order is the result of the confirmation process of the PO. The compliance checking process and process mapping are the features it can provide.
The delivery process of the orders
This is again the most important function that Ana needs in the system.twill teel her about the final payment details and the quantity of the product that is ordered by the customer and based on this information, Ana will proceed to add the packages for the customers.
The script is as following:
PizzaCentre.java
packagecom.pizza.main;
importjava.util.HashMap;
importjava.util.List;
importjava.util.Map;
importjava.util.Map.Entry;
importjava.util.Optional;
importjava.util.Scanner;
importcom.pizza.model.FoodItem;
importcom.pizza.model.Pasta;
importcom.pizza.model.Pizza;
importcom.pizza.model.SideItem;
public class PizzaCentre {
public static void main(String[] args) {
System.out.println(“Welcome to Pizza Centre..”);
Scanner sc = new Scanner(System.in);
inttotalPizzaInSession = 0;
inttotalPastaInSession = 0;
inttotalIncomeInSession = 0;
while(true) {
System.out.println(“Please select from the following options:”);
System.out.println(“1. Select Item”);
System.out.println(“2. Exit”);
String option = sc.nextLine();
if(!option.matches(“1|2”)) {
System.out.println(“You have selected incorrect option!!”);
continue;
}
if(option.equals(“1”)) {
inttotalPizza = 0;
inttotalPasta = 0;
inttotalPizzaPrice = 0;
inttotalPastaPrice = 0;
Map<String, FoodItem>foodItems = new HashMap<>();
booleanisPizzaAdded = false;
booleanisPastaAdded = false;
FoodItem pizza = null;
FoodItem pasta = null;
while(true) {
System.out.println(“Please select from the following items:”);
System.out.println(“1. Pizza”);
System.out.println(“2. Pasta”);
option = sc.nextLine();
if(!option.matches(“1|2”)) {
System.out.println(“You have selected incorrect option!!”);
continue;
}
System.out.println(“Enter the quantity of the item”);
int quantity = Integer.parseInt(sc.nextLine());
if(option.equals(“1”)) {
if(!isPizzaAdded) {
pizza = new Pizza();
}
totalPizzaInSession += quantity;
totalPizza += quantity;
isPizzaAdded = true;
pizza.setQuantity(totalPizza);
foodItems.put(“pizza”, pizza);
}else if(option.equals(“2”)){
if(!isPastaAdded) {
pasta = new Pasta();
}
totalPastaInSession += quantity;
totalPasta += quantity;
isPastaAdded = true;
pasta.setQuantity(totalPasta);
foodItems.put(“pasta”, pasta);
}
System.out.println(“Do you want to add more items? Y/N”);
option = sc.nextLine();
if(option.equalsIgnoreCase(“y”)) {
continue;
}else {
List<SideItem>sideItemList = null;
for(Entry<String, FoodItem> entry : foodItems.entrySet()) {
entry.getValue().calculatePrice();
if(entry.getKey().equals(“pizza”)) {
totalPizzaPrice = entry.getValue().getTotalPrice();
}else if(entry.getKey().equals(“pasta”)) {
totalPastaPrice = entry.getValue().getTotalPrice();
}
}
isPizzaAdded = false;
isPastaAdded = false;
sideItemList = FoodItem.checkForAdditionalOffers(foodItems);
String sideItemsString = “”;
if(sideItemList!=null && !sideItemList.isEmpty()) {
Optional<String>itemString = sideItemList.stream().map(x ->x.getQuantity() + “-” + x.getName()).reduce((x,y) -> x+”,”+y);
sideItemsString = itemString.get();
}
totalIncomeInSession += totalPastaPrice + totalPizzaPrice;
System.out.println(“Your Order details are as follows: “);
System.out.println(“Total no. of Pizzas: ” + totalPizza);
System.out.println(“Total no. of Pastas: ” + totalPasta);
System.out.println(“Total sideItems: ” + sideItemsString);
System.out.println(“Total payment amount of pizza in the current order: ” + totalPizzaPrice);
System.out.println(“Total payment amount of pasta in the current order: ” + totalPastaPrice);
System.out.println(“Total pizzas ordered in this session: ” + totalPizzaInSession);
System.out.println(“Total pastas ordered in this session: ” + totalPastaInSession);
System.out.println(“Total income in this session: ” + totalIncomeInSession);
break;
}
}
}else {
System.out.println(“Thanks for using this application..”);
break;
}
}
sc.close();
}
}
Pizza.java
packagecom.pizza.model;
public class Pizza implements FoodItem{
privateinttotalPrice;
privateint quantity;
@Override
public void calculatePrice() {
switch(quantity) {
case 1:
totalPrice = 12;
break;
case 2:
totalPrice = 22;
break;
default:
totalPrice = quantity*10;
break;
}
}
publicintgetTotalPrice() {
returntotalPrice;
}
publicintgetQuantity() {
return quantity;
}
public void setQuantity(int quantity) {
this.quantity = quantity;
}
}
Pasta.java
packagecom.pizza.model;
public class Pasta implements FoodItem{
privateinttotalPrice;
privateint quantity;
@Override
public void calculatePrice() {
switch(quantity) {
case 1:
totalPrice = 8;
break;
case 2:
totalPrice = 15;
break;
default:
totalPrice = quantity*7;
break;
}
}
publicintgetTotalPrice() {
returntotalPrice;
}
publicintgetQuantity() {
return quantity;
}
public void setQuantity(int quantity) {
this.quantity = quantity;
}
}
SideItem.java
packagecom.pizza.model;
publicenumSideItem{
GARLIC_BREAD(“Garlic Bread”,0,0),
SOFT_DRINK(“Soft Drink”,0,0),
BAKLAVA(“Baklava”,0,0);
private String name;
privateint quantity;
privateint price;
SideItem(String name, int quantity, int price){
this.name = name;
this.quantity = quantity;
this.price = price;
}
public String getName() {
return name;
}
public void setName(String name) {
this.name = name;
}
publicintgetQuantity() {
return quantity;
}
public void setQuantity(int quantity) {
this.quantity = quantity;
}
publicintgetPrice() {
return price;
}
public void setPrice(int price) {
this.price = price;
}
}
FoodItem.java
packagecom.pizza.model;
importjava.util.ArrayList;
importjava.util.List;
importjava.util.Map;
importjava.util.Map.Entry;
public interface FoodItem {
public void calculatePrice();
public static List<SideItem>checkForAdditionalOffers(Map<String, FoodItem>foodItems) {
intpizzaQuantity = 0;
intpastaQuantity = 0;
List<SideItem>sideItemList = new ArrayList<>();
for(Entry<String, FoodItem> entry : foodItems.entrySet()) {
if(entry.getKey().equals(“pizza”)) {
pizzaQuantity = entry.getValue().getQuantity();
}if(entry.getKey().equals(“pasta”)) {
pastaQuantity = entry.getValue().getQuantity();
}
}
if(pizzaQuantity>=3 || pastaQuantity>=3) {
int a = pizzaQuantity/3;
int b = pastaQuantity/3;
if(a>0) {
SideItemsideItem = SideItem.GARLIC_BREAD;
sideItem.setQuantity(a);
sideItemList.add(sideItem);
}
if(b>0) {
SideItemsideItem = SideItem.SOFT_DRINK;
sideItem.setQuantity(b);
sideItemList.add(sideItem);
}
int c = a < b? a: b;
if(pizzaQuantity>=3 &&pastaQuantity>=3) {
c = c==0? ++c : c;
SideItemsideItem = SideItem.BAKLAVA;
sideItem.setQuantity(c);
sideItemList.add(sideItem);
}
}
returnsideItemList;
}
publicintgetQuantity();
public void setQuantity(int quantity);
publicintgetTotalPrice();
}
Pizza Corner
package com.pizza.main;
import java.util.ArrayList;
import java.util.List;
import java.util.Scanner;
import com.pizza.model.BillingDO;
import com.pizza.service.ComplimentaryPasta;
import com.pizza.service.ComplimentaryPizza;
import com.pizza.service.PastaPaymentsImpl;
import com.pizza.service.Payments;
import com.pizza.service.PizzaPaymentsImpl;
public class PizzaCorner {
public static int sessionPizza = 0;
public static int sessionPasta = 0;
public static int sessionBilliAmount=0;
public static void main(String[] args) {
System.out.println(“Welcome to Pizza Kitchen!!!”);
System.out.println(“Please place your order here…”);
System.out.println(“***Today’s Special Offer, for every 3 Pizzas AND 3 Pasta Baklava (a famous dessert) is free***”);
Scanner sc = new Scanner(System.in);
boolean icorrectInput=false;
BillingDO billingDO = new BillingDO();
Payments pizzaPayments = new PizzaPaymentsImpl();
Payments pastaPayments = new PastaPaymentsImpl();
while(true) {
menu();
if(!sc.hasNext(“[0-9]+”)) {
icorrectInput = true;
System.out.println(“Not a valid input!Please try again.”);
break;
}
int selection = sc.nextInt();
if(selection==1) {
System.out.println(“We are offering following packages for Pizza \n”+
“1 Large Pizza : 12 AUD \n”+
“2 Large Pizzas : 22 AUD \n”+
“3 or more Pizzas 10 AUD per unit compliemntary garlic bread \nfor every three pizzas”);
System.out.println(“Provide the number of Pizza to be ordered..”);
int noOfPizza = sc.nextInt();
billingDO = pizzaPayments.payment(noOfPizza,billingDO);
System.out.println(“Do you want to add anything?”);
}else if(selection==2) {
System.out.println(“We are offering following packages for Pasta \n”+
“1 Large Pasta : 8 AUD \n”+
“2 Large Pasta : 15 AUD \n”+
“3 or more Pastas 7 AUD per unit compliemntary Soft Drink(1.25 Liter) \nfor every three pastas”);
System.out.println(“Provide the number of Pasta to be ordered..”);
int noOfPasta = sc.nextInt();
billingDO = pastaPayments.payment(noOfPasta,billingDO);
System.out.println(“Do you want to add more items in your order?”);
}else if(selection==3) {
System.out.println(“Thanks for shopping with us..Enjoy your meal!!”);
if(!icorrectInput){
billingDO=checkComplimentary(billingDO);
int totalAmount =billingDO.getPizzaPrice()+billingDO.getPastaPrice();
sessionPizza = sessionPizza+billingDO.getQuantPizza();
sessionPasta = sessionPasta+billingDO.getQuantPasta();
sessionBilliAmount = sessionBilliAmount+totalAmount;
System.out.println(“Total Payment for Pasta Order: “+billingDO.getPastaPrice()+” AUD”);
System.out.println(“Total Payment for Pizza Order: “+billingDO.getPizzaPrice()+” AUD”);
System.out.println(“Total Bill: “+totalAmount+” AUD”);
System.out.println(“Total items: “);
System.out.println(billingDO.getQuantPizza()+” Pizza(s) “+billingDO.getQuantPasta()+” Pasta(s).”);
if(!billingDO.getComplimentary().isEmpty()) {
System.out.println(“Enjoy your complimentary items: “);
billingDO.getComplimentary().forEach((n) -> System.out.println(n));
}
System.out.println(“Session Pizza Order: “+sessionPizza);
System.out.println(“Session Pasta Order: “+sessionPasta);
System.out.println(“Session Total Amount: “+sessionBilliAmount+” AUD”);
billingDO = new BillingDO();
}
continue;
}
else if(selection==4) {
System.out.println(“Session Pizza Order: “+sessionPizza);
System.out.println(“Session Pasta Order: “+sessionPasta);
System.out.println(“Session Total Amount: “+sessionBilliAmount+” AUD”);
System.out.println(“Thanks for visiting Pizza Kitchen!!”);
break;
}else {
System.out.println(“Provided input is incorrect.Please provide a valid value from below choices.”);
continue;
}
}
sc.close();
}
public static void menu() {
System.out.println(“1. Pizza”);
System.out.println(“2. Pasta”);
System.out.println(“3. Generate Bill & Continue with App”);
System.out.println(“4. Exit”);
}
public static BillingDO checkComplimentary(BillingDO billingDO) {
List<String> compItems = new ArrayList<>();
ComplimentaryPizza complimentary = new ComplimentaryPizza();
ComplimentaryPasta complimentaryPasta = new ComplimentaryPasta();
compItems.add(complimentary.complimentaryPizza(billingDO));
compItems.add(complimentaryPasta.complimentaryPasta(billingDO));
if(billingDO.getQuantPasta()>=3 && billingDO.getQuantPizza()>=3) {
compItems.add(complimentary.complimentaryPizzaPasta(billingDO));
}
billingDO.setComplimentary(compItems);
return billingDO;
}
}
Functionality to process the orders of various amount
Billing Do
package com.pizza.model;
import java.util.List;
public class BillingDO {
private int pizzaPrice;
private int quantPizza;
private int quantPasta;
private int pastaPrice;
private List<String> complimentary;
public int getPizzaPrice() {
return pizzaPrice;
}
public void setPizzaPrice(int pizzaPrice) {
this.pizzaPrice = pizzaPrice;
}
public int getPastaPrice() {
return pastaPrice;
}
public void setPastaPrice(int pastaPrice) {
this.pastaPrice = pastaPrice;
}
public int getQuantPizza() {
return quantPizza;
}
public void setQuantPizza(int quantPizza) {
this.quantPizza = quantPizza;
}
public int getQuantPasta() {
return quantPasta;
}
public void setQuantPasta(int quantPasta) {
this.quantPasta = quantPasta;
}
public List<String> getComplimentary() {
return complimentary;
}
public void setComplimentary(List<String> complimentary) {
this.complimentary = complimentary;
}
}
Additional Package 1
package com.pizza.service;
import java.util.ArrayList;
import java.util.List;
import com.pizza.model.BillingDO;
public class Complimentary {
public String complimentaryPizzaPasta(BillingDO billingDO) {
List<String> comp =new ArrayList<>();
comp.add(“Baklava (Dessert)”);
String complimentary=””;
int noOfBaklava =0;
int pasta =0;
int pizza =0;
if(billingDO.getQuantPasta()>=3) {
pasta = billingDO.getQuantPasta() / 3;
}
if(billingDO.getQuantPizza()>=3) {
pizza = billingDO.getQuantPizza() / 3;
}
if(pizza>=1 && pasta>=1) {
if(pizza>pasta) {
noOfBaklava = pasta;
}else if(pasta>pizza) {
noOfBaklava = pizza;
}else if(pasta==pizza) {
noOfBaklava = pasta;
}
complimentary = noOfBaklava+” “+comp.get(0);
}
return complimentary;
}
}
Additional Package 2
package com.pizza.service;
import java.util.ArrayList;
import java.util.List;
import com.pizza.model.BillingDO;
public class ComplimentaryPasta extends Complimentary{
public String complimentaryPasta(BillingDO billingDO) {
List<String> compPizza =new ArrayList<>();
compPizza.add(“Soft Drink(s) – 1.25 Liter”);
String complimentary=””;
int drinks = 0;
if(billingDO.getQuantPasta()>=3) {
drinks = billingDO.getQuantPasta() / 3;
}
complimentary = drinks+” “+compPizza.get(0);
return complimentary;
}
}
Additional Package 3
package com.pizza.service;
import java.util.ArrayList;
import java.util.List;
import com.pizza.model.BillingDO;
public class ComplimentaryPizza extends Complimentary{
public String complimentaryPizza(BillingDO billingDO) {
List<String> compPizza =new ArrayList<>();
compPizza.add(“Garlic Bread(s)”);
int garlicBreads = 0;
String complimentary;
if(billingDO.getQuantPizza()>=3) {
garlicBreads = billingDO.getQuantPizza() / 3;
}
complimentary = garlicBreads+” “+compPizza.get(0);
return complimentary;
}
}
Payments
package com.pizza.service;
import com.pizza.model.BillingDO;
public interface Payments {
BillingDO payment(int quantity, BillingDO billingDO);
}
A progressive payments menu option that displays the total income received
from both the items (pizza & pasta) individually and the total income from all
orders
Payments for Pizza
package com.pizza.service;
import com.pizza.model.BillingDO;
public class PizzaPaymentsImpl implements Payments{
@Override
public BillingDO payment(int quantity, BillingDO billingDO) {
int quant = billingDO.getQuantPizza()+quantity;
int price=0;
if(billingDO.getQuantPizza()==0) {
billingDO.setQuantPizza(quantity);
}else {
billingDO.setQuantPizza(quantity+billingDO.getQuantPizza());
}
if(quant==1) {
price = 12;
}else if(quant==2) {
price = 22;
}else if(quant>=3) {
price = quant*10;
}
billingDO.setPizzaPrice(price);
return billingDO;
}
}
Payments for Pasta
package com.pizza.service;
import com.pizza.model.BillingDO;
public class PastaPaymentsImpl implements Payments{
@Override
public BillingDO payment(int quantity, BillingDO billingDO) {
int quant = billingDO.getQuantPasta()+quantity;
int price=0;
if(billingDO.getQuantPasta()==0) {
billingDO.setQuantPasta(quantity);
}else {
billingDO.setQuantPasta(quantity+billingDO.getQuantPasta());
}
if(quant==1) {
price = 8;
}else if(quant==2) {
price = 15;
}else if(quant>=3) {
price = quant*7;
}
billingDO.setPastaPrice(price);
return billingDO;
}
}
Project
<?xml version=”1.0″ encoding=”UTF-8″?>
<projectDescription>
<name>PizzaKitchen</name>
<comment></comment>
<projects>
</projects>
<buildSpec>
<buildCommand>
<name>org.eclipse.jdt.core.javabuilder</name>
<arguments>
</arguments>
</buildCommand>
</buildSpec>
<natures>
<nature>org.eclipse.jdt.core.javanature</nature>
</natures>
</projectDescription>
Class Path
<?xml version=”1.0″ encoding=”UTF-8″?>
<classpath>
<classpathentry kind=”con” path=”org.eclipse.jdt.launching.JRE_CONTAINER/org.eclipse.jdt.internal.debug.ui.launcher.StandardVMType/JavaSE-1.8″/>
<classpathentry kind=”src” path=”src”/>
<classpathentry kind=”output” path=”bin”/>
</classpath>
Settings pre requirement
eclipse.preferences.version=1
org.eclipse.jdt.core.compiler.codegen.inlineJsrBytecode=enabled
org.eclipse.jdt.core.compiler.codegen.targetPlatform=1.8
org.eclipse.jdt.core.compiler.codegen.unusedLocal=preserve
org.eclipse.jdt.core.compiler.compliance=1.8
org.eclipse.jdt.core.compiler.debug.lineNumber=generate
org.eclipse.jdt.core.compiler.debug.localVariable=generate
org.eclipse.jdt.core.compiler.debug.sourceFile=generate
org.eclipse.jdt.core.compiler.problem.assertIdentifier=error
org.eclipse.jdt.core.compiler.problem.enumIdentifier=error
org.eclipse.jdt.core.compiler.release=disabled
org.eclipse.jdt.core.compiler.source=1.8
Code demonstrating the use of an interface and polymorphism to handle the item
fires and the various item options available
Billing of orders
Billing in the Same session
Invalid input from the choice
Invalid input from the choice
Reflection on learning
The information that is required to complete this assessment and the tasks are collected and the concepts are developed and learned on a practical basis. The man interesting learning that I gained from completing this assignment is that the basic concepts are used in the practical approach and to solve a problem similar to the real-life issue. The interesting details and the techniques to identify the use cases before implementing and preparing the programming for developing an application or such system as it is described in the assignment. The requirements that play a major role to define and identify the use cases are studied and the other details and important features are also reviewed. The main purpose of the UML diagrams is to understand. After knowing the main function of the UML diagrams, the detailed diagrams are prepared that represent the Use cases, classes, and sequence of the processes and operation that complete the customers’ orders. The code is developed and the programming is done as per the requirements of the system that Ana wants to implement. The object-oriented programming language JAVA is used for the development of the code and the systems to display the men and the ament details. Thus this assessment helped to understand the theoretical concepts like polymorphism and uses of classes in the practical learning exercise.
References
- Chavan, V., Jadhav, P., Korade, S., & Teli, P. (2015). Implementing customizable online food ordering system using web based application. International Journal of Innovative Science, Engineering & Technology, 2(4), 722-727.
- Susanto, T., Djamaris, A. R., & Azkia, N. (2016). Process Analysis on Order Processing Function to Reduce Order Processing Time: Indonesian Context. International Journal of Research in Management & Technology (IJRMT), 76-89.
- Tanpure, S. S., Shidankar, P. R., & Joshi, M. M. (2013). Automated food ordering system with real-time customer feedback. International Journal of Advanced Research in Computer Science and Software Engineering, 3(2).
Create a new database.
| — phpMyAdmin SQL Dump
— version 5.0.2
— https://www.phpmyadmin.net/
—
— Host: 127.0.0.1
— Generation Time: Apr 23, 2020 at 06:55 PM
— Server version: 10.4.11-MariaDB
— PHP Version: 7.4.4
SET SQL_MODE = “NO_AUTO_VALUE_ON_ZERO”;
START TRANSACTION;
SET time_zone = “+00:00”;
/*!40101 SET @OLD_CHARACTER_SET_CLIENT=@@CHARACTER_SET_CLIENT */;
/*!40101 SET @OLD_CHARACTER_SET_RESULTS=@@CHARACTER_SET_RESULTS */;
/*!40101 SET @OLD_COLLATION_CONNECTION=@@COLLATION_CONNECTION */;
/*!40101 SET NAMES utf8mb4 */;
—
— Database: `myuniversity`
—
CREATE DATABASE IF NOT EXISTS `myuniversity` DEFAULT CHARACTER SET utf8mb4 COLLATE utf8mb4_general_ci;
USE `myuniversity`; |
Create the tables
— Indexes for dumped tables
—
—
— Indexes for table `class`
—
ALTER TABLE `class`
ADD PRIMARY KEY (`classID`) USING BTREE,
ADD KEY `FK2` (`LectureID`),
ADD KEY `FK1` (`CourseID`),
ADD KEY `FK3` (`RoomID`);
—
— Indexes for table `course`
—
ALTER TABLE `course`
ADD PRIMARY KEY (`CourseID`);
—
— Indexes for table `lecturer`
—
ALTER TABLE `lecturer`
ADD PRIMARY KEY (`LecturerID`),
ADD UNIQUE KEY `LecturerID` (`LecturerID`);
—
— Indexes for table `room`
—
ALTER TABLE `room`
ADD PRIMARY KEY (`RoomID`),
ADD UNIQUE KEY `RoomID` (`RoomID`);
—
— AUTO_INCREMENT for dumped tables
—
—
— AUTO_INCREMENT for table `class`
—
ALTER TABLE `class`
MODIFY `classID` int(11) NOT NULL AUTO_INCREMENT, AUTO_INCREMENT=7129;
—
— Constraints for dumped tables
—
—
— Constraints for table `class`
—
ALTER TABLE `class`
ADD CONSTRAINT `FK1` FOREIGN KEY (`CourseID`) REFERENCES `course` (`CourseID`),
ADD CONSTRAINT `FK2` FOREIGN KEY (`LectureID`) REFERENCES `lecturer` (`LecturerID`),
ADD CONSTRAINT `FK3` FOREIGN KEY (`RoomID`) REFERENCES `room` (`RoomID`);
—
— Metadata
—
USE `phpmyadmin`;
—
— Metadata for table class
—
—
— Metadata for table course
—
—
— Metadata for table lecturer
—
—
— Metadata for table room
—
—
— Metadata for database myuniversity
—
—
— Dumping data for table `pma__pdf_pages`
—
INSERT INTO `pma__pdf_pages` (`db_name`, `page_descr`) VALUES
(‘myuniversity’, ‘schema’);
SET @LAST_PAGE = LAST_INSERT_ID();
—
— Dumping data for table `pma__table_coords`
—
INSERT INTO `pma__table_coords` (`db_name`, `table_name`, `pdf_page_number`, `x`, `y`) VALUES
(‘myuniversity’, ‘class’, @LAST_PAGE, 402, 143),
(‘myuniversity’, ‘course’, @LAST_PAGE, 638, 31),
(‘myuniversity’, ‘lecturer’, @LAST_PAGE, 640, 137),
(‘myuniversity’, ‘room’, @LAST_PAGE, 651, 231);
—
— Dumping data for table `pma__pdf_pages`
—
INSERT INTO `pma__pdf_pages` (`db_name`, `page_descr`) VALUES
(‘myuniversity’, ‘schema2’);
SET @LAST_PAGE = LAST_INSERT_ID();
—
— Dumping data for table `pma__table_coords`
—
INSERT INTO `pma__table_coords` (`db_name`, `table_name`, `pdf_page_number`, `x`, `y`) VALUES
(‘myuniversity’, ‘class’, @LAST_PAGE, 402, 143),
(‘myuniversity’, ‘course’, @LAST_PAGE, 638, 31),
(‘myuniversity’, ‘lecturer’, @LAST_PAGE, 640, 137),
(‘myuniversity’, ‘room’, @LAST_PAGE, 651, 231);
Create the relationships between the tables
—
— Table structure for table `class`
—
DROP TABLE IF EXISTS `class`;
CREATE TABLE `class` (
`classID` int(11) NOT NULL,
`CourseID` varchar(8) NOT NULL,
`LectureID` int(11) NOT NULL,
`RoomID` varchar(4) NOT NULL,
`Day` char(4) NOT NULL,
`Time` time(3) NOT NULL,
`Length` int(11) NOT NULL
) ENGINE=InnoDB DEFAULT CHARSET=utf8mb4;
—
— RELATIONSHIPS FOR TABLE `class`:
— `CourseID`
— `course` -> `CourseID`
— `LectureID`
— `lecturer` -> `LecturerID`
— `RoomID`
— `room` -> `RoomID`
—
—
— Dumping data for table `class`
—
INSERT INTO `class` (`classID`, `CourseID`, `LectureID`, `RoomID`, `Day`, `Time`, `Length`) VALUES
(2483, ‘ENG402’, 1234, ‘A24’, ‘mond’, ’11:00:18.000′, 9),
(7128, ‘MAT401’, 7890, ‘B26’, ‘tues’, ’15:00:18.000′, 7);
Viewing the relationships between tables: WampServer also provides a way to view the relationships between the tables.
—
— Table structure for table `course`
—
DROP TABLE IF EXISTS `course`;
CREATE TABLE `course` (
`CourseID` varchar(9) NOT NULL,
`CourseName` text NOT NULL,
`Description` text NOT NULL,
`CreditPoints` int(11) NOT NULL
) ENGINE=InnoDB DEFAULT CHARSET=utf8mb4;
—
— RELATIONSHIPS FOR TABLE `course`:
—
—
— Dumping data for table `course`
—
INSERT INTO `course` (`CourseID`, `CourseName`, `Description`, `CreditPoints`) VALUES
(‘ENG402’, ‘ENGLISH’, ‘English Literature class.’, 10),
(‘MAT401’, ‘MATHS’, ‘Mathematical class’, 10);
Inserting data into a table
—
— Table structure for table `lecturer`
—
DROP TABLE IF EXISTS `lecturer`;
CREATE TABLE `lecturer` (
`LecturerID` int(11) NOT NULL,
`LecturerFirstname` text NOT NULL,
`LecturerSurname` text NOT NULL
) ENGINE=InnoDB DEFAULT CHARSET=utf8mb4;
—
— RELATIONSHIPS FOR TABLE `lecturer`:
—
—
— Dumping data for table `lecturer`
—
INSERT INTO `lecturer` (`LecturerID`, `LecturerFirstname`, `LecturerSurname`) VALUES
(1234, ‘Evan’, ‘Woods’),
(7890, ‘Olivia’, ‘Patrick’);
| — ——————————————————–
—
— Table structure for table `room`
—
DROP TABLE IF EXISTS `room`;
CREATE TABLE `room` (
`RoomID` varchar(4) NOT NULL,
`RoomType` text NOT NULL,
`Building` varchar(4) NOT NULL
) ENGINE=InnoDB DEFAULT CHARSET=utf8mb4;
—
— RELATIONSHIPS FOR TABLE `room`:
—
—
— Dumping data for table `room`
—
INSERT INTO `room` (`RoomID`, `RoomType`, `Building`) VALUES
(‘A24’, ‘Single’, ‘ABC’),
(‘B26’, ‘Double’, ‘xyz’); |
References
- Dev.mysql, 2020. About Creating and Selecting a Database. Dev.mysql. Available at – https://dev.mysql.com/doc/refman/8.0/en/creating-database.html. [Accessed on – 25 April 2020].
- Digitalocean.com, 2020. About A Basic MySQL Tutorial. Digitalocean.com. Available at – https://www.digitalocean.com/community/tutorials/a-basic-mysql-tutorial. [Accessed on – 25 April 2020].
- Docs.kony, 2020. About Database Setup Guide-MySQL. Docs.kony. Available at – https://docs.kony.com/5_0/docs/databasedocuments/mysql/KonyDatabaseSetupGuide-MySQL.pdf. [Accessed on – 25 April 2020].
- Docs.oracle, 2020. About MySQL Database Installation and Configuration for Advanced Management Console. Docs.oracle. Available at – https://docs.oracle.com/javacomponents/advanced-management-console-2/install-guide/mysql-database-installation-and-configuration-advanced-management-console.htm#JSAMI116. [Accessed on – 25 April 2020].
- Downloads.mysql, 2020. About MySQL Tutorial. Downloads.mysql. Available at – https://downloads.mysql.com/docs/mysql-tutorial-excerpt-5.7-en.pdf. [Accessed on – 25 April 2020].
Introduction
Task that given in this assignment is to create a state transition diagram for the case scenario given. the case that is given in this assignment is about a toothbrush known as Oral-b Braun 5000. It is launched by toothpaste company name Oral B. State transition diagram is created on the basis of personality and flow provided by the system of this toothbrush.
The creation of diagram is done to showcase the understanding of learning outcome of this course. the diagrams are also properly explained so that each key activity that are done in that state transactions are properly understandable for functionality in toothbrush. After the analysis of diagram state guide is also created that involve various test cases for this product. Report contains various facilities provided by the government to protect along with the functionality of its smart guide.
Functionalities of Oral B ‘s Braun 5000 toothbrush
There are many functionalities that are related to practice of this electric toothbrush in an efficient manner. Some of major functionalities are as follows-
Brushing technique-
Weather toothbrush is manual or it is an automatic major purpose of a toothbrush is to clean teeth effectively and provide a pleasing smell of breath. Process starts with applying toothpaste on head of an electrical toothbrush and put toothbrush in mouth properly before turning it on. After putting a toothbrush in mouth, it must be turned on. Toothbrush must shift to each tooth very properly and it must be hold on each tooth for some seconds so that effective cleaning can take place. If one wants one can change mode according to need. Time of brushing is almost same as an ordinary brush. Functioning of this brush is similar to a common brushing technique which makes it easy to use.
Timer
Next functionality is timer setting during brushing with this toothbrush. Basically, there are two types of timer available on this electric toothbrush first type is named as a professional timer which is of 30 seconds and second one is a two minute timer which is generally used by beginners. In first type, timer is set for 30 seconds and when 30 seconds are over then an alarm can be heard with a shuttering or vibrating sound, green light can be seen that indicates timer is over (Meyer-Wübbold, et al, 2019). This timer is for professionals as this is used for brushing teeth precisely over small portions of mouth with effective cleaning. Second type of timer is for beginners as we can set timer of two minutes which is not for cleaning mouth portion by portion this will clean mouth entirely in a single run. When timer is over a shuttering or vibrating type of sound can be heard along with green light signal just like first one. Thus, we can say these two types of timers provide flexibility according to user.
Timer personalising
This point tells us about flexibility with which we can set timer it is a very important point according to this point timer can be set whenever needed according to need quite easily. If a person is professional then there is a timer option of 30 seconds timer and if a user is a beginner then timer can be easily set for 2 minutes.
Cleaning action in 3D
Cleaning action obtained by this brush is way better than an ordinary brush as it provides cleaning action in all three dimensions with a very smooth experience.
Pressure sensor
Main purpose of a pressure sensor is to check pressure regularly and balance it according to requirement if pressure is way too high and brush is providing uncomfortable brushing experience then it lower pressure to a certain value. And if pressure is very less so that it is not giving effective cleaning then it increases pressure according to requirement (Ccahuana‐Vasquez, et al, 2019).
Bluetooth connectivity to Oral B application
Users can also connect toothbrushes with app of Oral B through Bluetooth. This is a very unique feature which is not found in these types of devices. This feature provides extra flexibility in usage of this electrical toothbrush.
Major purpose served by Oral B’s Braun 5000 brush
Above mentioned all functionalities completely explains how to use this electrical toothbrush in an effective manner. a major purpose of type of toothbrush whether it is electrical or ordinary is to clean teeth effectively along with pleasant smell breath which must last long. After applying paste on head of toothbrush it must be put in mouth and one must make sure it reaches to each and every tooth. This brush is way easier to operate comparing it to simple brushes but it serves same purpose with more effective cleaning (Anas, et. al, 2018).
Oral B’s Braun 5000 using guide functionalities
There are many functionalities and all of them contain functions that guide us to usage of oral B’s Braun 5000 toothbrush. Some of major functionalities are as follows:
Brushing timer -It’s first and most important point which tells us that timer is very flexible and it can be easily defined according to different requirements at different times. So basically, there can be seen two types of timer. first one is a timer of 2 minutes when two minutes are over It produces a short vibrating sound with a signal of green light (Dhir and Kumar, 2018). second type of timer is professional timer this timer is for only 30 seconds when 30 seconds are over it acts as same like first one and produces short vibrating sound along with a signal of green light. This timer is more useful for experienced users if a user wants to brush teeth portion by portion with supreme efficiency then this type of timer will be useful in finishing job.
Quadrant indicator-It’s second important point of functionalities of brush. It can be seen on display of toothbrush and it plays a major role in brushing (Allocca, et al, 2018). Main purpose of this feature is to indicate which portion of mouth is required to be cleaned. And part which is to be cleaned is shown on display.
Pressure indicator for brushing- This part checks and controls pressure of brushing continuously during brushing process. It changes pressure according to different portions of mouth which are to be cleaned (Temiz and Yavuz, 2018).
Brushing modes- There are many modes available for brushing. These modes can be changed anytime according to different requirements. Modes can be changed anytime according to individual needs.
Usage as clock- Toothbrush can also be used as clock while its free and no one is brushing teeth. This a very fascinating feature of this electric toothbrush.
Charging and other connections- This includes various functionalities like how to use a toothbrush and what are basic things which must be taken care of while charging toothbrush. handle of toothbrush is waterproof and completely safe in electrical aspects. Because toothbrush is kept in bathroom so it is certain that it will come in contact with water regularly.
Major purpose of smart guide of Oral B’s Braun 5000 –
Smart guide of toothbrush basically explains all important things which must be taken care of while using a toothbrush. It tells users about how to use toothbrush safely and with greater efficiency (Grender, et al, 2020). All main functions and functionalities are properly explained in report so that a user can use toothbrush in an easy and efficient way.
Tool selection
There are many software available and among all provided options, an option which will be most appropriate to select is draw.io for creation of needed diagrams according to given description. This report contains transition diagram of state and with draw.io it is established.
Advantages of draw.io –
This tool is in application for storing diagrams on cloud. So main benefit of this tool is that it doesn’t use storage space of system. It is because it uses cloud storage for storing diagrams.
Main feature of draw.io-
First and main feature of this tool is that it is very easy to use both functionally and practically.
Even beginners can use it quite easily.
Another feature of draw.io is that it does not need to be downloaded and installed in system so it doesn’t occupy system storage. So that users will not need to worry about storage capacity of system.
State Transition Diagram
For oral B’s Braun 5000 electric toothbrush

Figure 1: Braun 5000’s State Transition Diagram
Above shown diagram is diagram for state transition of Oral-B’s Braun 5000 toothbrush. This diagram tells us how functioning of toothbrush starts step by step and what are main processes that are done in toothbrush (Ratanakongnate and Makmun, 2017). Major purpose of Oral-B’s Braun 5000 is to clean teeth in an efficient way so that each corner of mouth gets cleaned and breath of user is filled with good smell. Application of toothbrush starts with applying some toothpaste on head of an electric toothbrush. Then it must be inserted in mouth and applied to all portions of mouth with holding toothbrush on each tooth for some seconds.
When toothbrush is turned on first of all battery level is get checked if battery is charged enough than next process starts and if battery is not charged enough then toothbrush is needed to connect to charger. After that selection of timer must be done from two different types of timer. If user is professional then he must choose second type of timer. Next phase is pressure checking if pressure exceeds from required level then it will get decreased automatically and if pressure is lower than it will get increased to required level. After that next phase is selection of mode as there are different modes available one must choose mode according to requirement. As some modes need specific head so one must change head according to selected mode. After all these processes brushing of teeth starts and all these processes take place in fraction of microseconds.
Smart guide for Braun 5000 electric toothbrush-
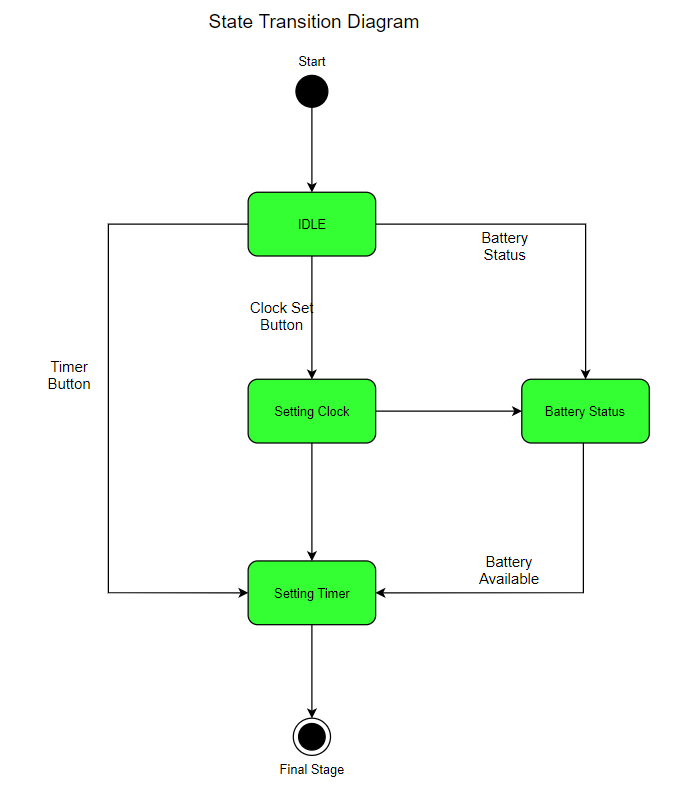
Figure 2: Smart Guide State Transition Diagram
Above diagram tells us about smart guide of Oral B’s Braun 5000 electric toothbrush. This diagram is designated as diagram of state transition (Pires, et al., 2018). This diagram explains all steps of smart guide of toothbrush. Main purpose of this smart guide is to tell users how to use toothbrush. This smart guide has many functionalities and these functionalities guide users about how to use it. First of all, users need to press set button for setting up timers for brushing process. When user press set button then if battery isn’t charged then it is indicated by battery indicator. Then user has to press timer button and set time for clock. Most ideal time is 30 seconds. If battery is not charged then it will be charged and then process will continue.
Test cases –
Table 1: Various Test cases
| S. No |
Test Case |
Supposed Results |
Original Results |
| 1. |
Brush Charging |
Yellow Light Shows Up |
It is Correct |
| 2. |
Low Level of Charge. |
Red Light Shows Up |
It is Correct |
| 3. |
Increasing 2 min interval. |
Shuttering Noise Heard |
It is Correct |
| 4. |
Implementing too much pressure. |
Sets Itself on Auto mode |
It is Correct |
Test cases shown above are explained in tabular form. These test cases are associated with usage of Oral-B’s electric toothbrush. In above shown table test cases are arranged with expected results and actual results. So, it is basically comparison between expected and actual results. First test case is related to charging process this is noticed on most of electric items.
First test case is associated with charging of toothbrush expected result of first case is blowing of yellow light that indicate charging process and in actual we have obtained same result as expected. Second test case is related to low charging of toothbrush which is expected with turning on red light and we have obtained actual result as expected. Thus, it passed this test as expected. Third case is related to if 2 mins interval is increased or not so in expected result shuttering or vibrating sound must occur and in actual, we have obtained same results thus this case is also passed by toothbrush. Next test case which is also final test case is about what happens during excessive pressure so expected outcome is that auto-switch must get on and in actuality we have obtained same result. Thus, we can say it has passed this test too quiet accurately. All four test cases are passed by toothbrush as all expected results match with true outcomes.
Conclusion
This report contains detail about state transition diagram of Oral-B’s Braun 5000 toothbrush. This report also contains all information about Oral B; s Braun 5000 brush along with this toothbrush’s smart guide. It has all explanations related to functionalities of toothbrush. One part of report also explains about test cases of toothbrush and comparison of expected results with actual results.
Tool which is used is draw.io which is explained along with its benefits. All features of draw.io are explained in report properly. Report contain all functionalities and functions of toothbrush as well as its smart guide. Main purpose of toothbrush is very well explained in report. Major purpose of toothbrush is effective cleaning in each and every part of mouth with pleasant smell in breath. Purpose of this toothbrush is no different than a normal toothbrush but it serves it purpose in a more efficient way. And it is easier to operate than an ordinary toothbrush. It is also provided with some excellent digital capabilities like Bluetooth connectivity and timer setting etc.
References
Dhir, S. and Kumar, V., 2018. Efficacy of oscillating–Rotating toothbrush (Oral–B) on periodontal health-A 4 week controlled clinical and microbiologic study. Journal of the International Clinical Dental Research Organization, 10(1), p.12.
Temiz, B.K. and Yavuz, A., 2018. Simple wave drivers: electric toothbrush, shaver and razor. Physics Education, 53(3), p.033006.
Anas, B., ElM, M., Abdelhadi, M., Zahra, L.F. and Hamza, M., 2018. A Single-Brushing Study to Compare Plaque Removal Efficacy of a Manual Toothbrush, an Electric Toothbrush and an Ultrasonic Toothbrush. J Oral Hyg Health, 6(249), pp.2332-0702.
Ccahuana‐Vasquez, R.A., Adam, R., Conde, E., Grender, J.M., Cunningham, P., Goyal, C.R. and Qaqish, J., 2019. A 5‐week randomized clinical evaluation of a novel electric toothbrush head with regular and tapered bristles versus a manual toothbrush for reduction of gingivitis and plaque. International journal of dental hygiene, 17(2), pp.153-160.
Meyer-Wübbold, K., Günay, H. and Ebert, K., 2019. The effectiveness of an electric “wash toothbrush” on oral plaque control–A pilot study. Minimally invasive therapy of a late diagnosed Dentinogenesis imperfecta, 1, pp.175-181.
Allocca, G., Pudylyk, D., Signorino, F., Grossi, G.B. and Maiorana, C., 2018. Effectiveness and compliance of an oscillating-rotating toothbrush in patients with dental implants: a randomized clinical trial. International journal of implant dentistry, 4(1), p.38.
Grender, J., Goyal, C.R., Qaqish, J. and Adam, R., 2020. An 8‐week randomized controlled trial comparing the effect of a novel oscillating‐rotating toothbrush versus a manual toothbrush on plaque and gingivitis. International Dental Journal, 70, pp. S7-S15.
Pires, S.R., Pires, T.G. and Pires, D.G.F., 2018. Mapping and Simulation of Educational Games Using a State Transition Diagram and a Rules Base. US-China Education Review, 8(2), pp.61-72.
Ratanakongnate, S. and Makmun, P., 2017. Automated Generate Test Sequence from State Transition Diagram Using Ant Colony Optimization. International Journal of Computer Theory and Engineering, 9(3), p.156.
Introduction and description of project background
A business case refers to the first expected outcome in the life cycle of IT projects. It provides an assessment of the feasibility, value, benefits, risks and costs of various suggested options or alternatives to an organization (Panwar et al., 2017). The report shall present a business case based on Port Fairy Caravan and Camping Park. The company, which is based in Port Fairy, offers customers a wide range of options for accommodation such as non-motorized and motorized camping sites, recently renovated cabins consisting of a toilet, lounge, and kitchenette and shower room. The project undertaken by South West Advertising Inc. aims to analyze as well as evaluate the company’s e-marketing strategies by reviewing all e-marketing channels such as online newsletters, advertising on Google and social media, posts on community website and community notice boards.
Description of project objectives (including link to organisational mission statement)
The purpose of the project based on Port Fairy Caravan and Camping Park is to analyse the e-marketing strategy of the company. The evaluation must also provide details of a review and investigation into all e-marketing channels used by the company at present such as online newsletters, social media advertising, mobile app, and other platforms (Chaffey & Ellis-Chadwick, 2019). Furthermore, the project shall also provide a list of changes that are to be made in the bookings, ROI and comparison with key competitors, for each of the e-marketing channel used by Port Fairy Caravan Park. The director of Port Fairy, Jerry Maguire has realized that the digital marketing strategy of the company is extremely costly and therefore wants to review it for determining the most cost-friendly yet impactful approach to promote the park’s facilities on various online advertising platforms. This is even more urgent for the company since its mission is to be the leading camping and holiday spot for tourists at an affordable price range for packages (portfairycaravanparks.com, 2020).
Description of the current situation (including a SWOT analysis)
A SWOT analysis of the present situation at Port Fairy with regard to its e-marketing strategy review project has been presented.
Strengths
- The project is expected to derive the most impactful and economical approach to the digital marketing strategy implemented by Port Fairy Caravan Park
- The project is expected to make a minimum of 25% ROI.
|
Weaknesses
- Due to the difference in educational background, ideals, and skills of people on sports-related projects and those who work on new caravanning and camping projects, the project is on a weak ground.
- This difference has led to many employees not in full agreement with South West’s new strategies of concentrating on increasing profits by entering new markets.
|
Opportunities
- The project can review already-available information, carry out research and collect new material about the markets that are to be tapped in order to help employees gain insights about the new changes in the strategy.
- For ensuring the success of the tender bid, the project manager can evaluate the digital marketing strategy, review the current digital presence of Port Fairy and other such details in order to come up with the most economical and cost-effective e-marketing strategy for the company (Wirtz & Zeithaml, 2018)
|
Threats
-
- The shift to focus more on increasing profits by tapping into new markets can be quite challenging for South West, which predominantly focuses on the evaluation and development of e-marketing strategies for sporting companies (Hollensen, 2019).
- Threats can arise not only from key stakeholders such as employees but also from the suppliers due to the abrupt change in the company’s strategies.
|
Table 1: SWOT analysis of the current situation
Outline of problem/opportunity statement
The project aims to come up with the most cost-effective strategy for digital marketing for the company, Port Fairy that shall help the company’s director, Jerry Maguire to invest more on improving and optimising the facilities provided by the parks. The biggest expected opportunity of the project is that it shall lead to a minimum of 25% ROI. However, the company that has been chosen by him for this purpose, South West primarily focuses on evaluating digital marketing strategies for sports enterprises. The CEO of the firm wants to change the currently followed strategy by tapping into other markets such as reviewing digital marketing strategy of a caravanning company, Port Fairy. This move is expected to create numerous problems for the company due to the vast difference in the education and skills of the employees working on sporting companies and camping marketing projects.
Details of critical assumptions and constraints
With this project, it is assumed that the current costs and expenses involved in the online marketing strategy of Port Fairy would be minimised and the most impactful approach to market the services and facilities of the parks would be formulated. Furthermore, it is also assumed that the project shall earn a minimum of 25% ROI. Moreover, since the project evaluation will require data to support the findings and discussion made while reviewing the existing digital marketing strategies of the firm, it is assumed that this data and information would be gained through conducting surveys of the vacationers and reviewing and evaluating the financial records and bookings (Das et al., 2019).
However, the challenges are in the form of resistance from employees of South West Advertising who may not agree with the CEO, Bob Sugar’s interest in increasing the profits of the company by tapping into new markets, such as caravanning and camping marketing projects. Furthermore, the stark differences in the skill sets of the employees working on evaluating sporting firms’ e-marketing strategies and those of camping ones shall also constitute major constraints.
An analysis of options and recommendations
In order to overcome the potential challenges discussed above, South West Advertising would be required to gain significant knowledge and information about the current e-marketing channels used by Port Fairy. This is to be followed by convincing the employees who are unwilling to welcome the change in strategy to look at the finer sides of the new strategy in terms of the profits that shall be earned if the projects are successful (Noe & Kodwani, 2018). Lastly, training programs and workshops can be organised in order to train the employees to develop the basic skills that are required by them for evaluating camping e-marketing channels and strategies.
financial analysis (npv, roi and payback figures)
NPV
| Discount rate |
9.00% |
|
|
|
|
|
| |
|
|
|
|
|
|
| Assume the project is completed in Year 0 |
|
|
Year |
|
|
|
| |
0 |
1 |
2 |
3 |
Total |
|
| Costs |
90,000 |
20,000 |
20,000 |
15,000 |
|
|
| Discount factor |
1.00 |
0.92 |
0.84 |
0.77 |
|
|
| Discounted costs |
90,000 |
18,400 |
16,800 |
11,550 |
1,36,750 |
|
| |
|
|
|
|
|
|
| Benefits |
0 |
90,000 |
1,30,000 |
1,50,000 |
|
|
| Discount factor |
1.00 |
0.92 |
0.84 |
0.77 |
|
|
| Discounted benefits |
0 |
82,800 |
1,09,200 |
1,15,500 |
3,07,500 |
|
| |
|
|
|
|
|
|
| Discounted benefits – costs |
(90,000) |
64,400 |
92,400 |
1,03,950 |
|
NPV |
| Cumulative benefits – costs |
(90,000) |
|
66,800 |
1,70,750 |
|
|
| |
|
|
|
|
|
|
|
|
125% |
|
|
|
|
|
| |
Payback in Year 1 |
|
|
|
Table 1: NPV
IRR
| |
|
|
|
Present value |
| Year |
Cost |
Benefit |
Net cash flow |
at DF 80% |
at DF 90% |
| 0 |
-90000 |
0 |
-90000 |
-90000 |
-90000 |
| 1 |
-20000 |
90000 |
70000 |
38888.5 |
36842.4 |
| 2 |
-20000 |
130000 |
110000 |
33950.4 |
30471.1 |
| 3 |
-15000 |
150000 |
135000 |
23148.45 |
19681.65 |
| |
|
|
Total |
5987.35 |
-3004.85 |
Table 2: IRR
IRR = 80+(90-80)*5987.35/{5987.35-(-3004.85)}
= 86.66%
Payback Period
| Year |
Costs |
Benefits |
Cum Costs |
Cum Benefits |
| 0 |
90,000 |
0 |
90,000 |
0 |
| 1 |
20,000 |
90,000 |
1,10,000 |
90,000 |
| 2 |
20,000 |
1,30,000 |
1,30,000 |
2,20,000 |
| 3 |
15,000 |
1,50,000 |
1,45,000 |
3,70,000 |
Table 3: Payback period

Figure 1: Payback period
From the above calculation it can be seen that NPV of project in three months is going to be $170,750. IRR of the project is expected to be 86.66%. Payback period is going to 1 year. All these results are showing positive outcomes of new project. These tools are used to identify potential risks and profitability of project before making investment.
NPV shows the current value of money after a specific time. NPV is reflecting that value of project after 3 months would be $170,750. It means value is going to increase from $144,540 to $170,750. IRR shows the earnings from an investment on periodic basis. Rate of return is 86.66% it means project would earn $ 86.66 on spending each $100. Payback period shows the duration in which cost of an investment project would be recovered. Company can invest in new project as it would be profitable for company in future.
Preliminary project requirements (project preliminary scope)
| Project Justification |
Project is created to analyse Port fairy Carvan and Camping park pty Ltd e marketing strategy. It will also include the evaluation of all e marketing channels. |
| Product Description |
It would include evaluation of e marketing strategy, examination of current target market through survey and research. Information would be gathered from customers, market and employees about the new strategy. |
| Project deliverables |
a) Digital marketing strategy evaluation b) Research about customer profile C) analysis of digital channel d) evaluation of messaging strategy e) review of marketing ROI and recommendation for new e marketing strategy. |
| Project objective |
Objective is to evaluate e commerce strategy for Port fairy Carvan and identify ROI, NPV and PP. Motive is to complete project on time within budget. |
| Out of scope items |
Internal information of company such as traditional marketing and finances are out of scope items. All employees cannot be surveyed. |
| Cost objective |
Total estimated cost for project has been kept
$145,000. Therefore, activities would be allocated as per the budgeted amount. |
| Schedule objective |
Three months or 12 weeks have been considered for the completion of project. |
| Acceptance criteria |
Acceptance criteria reflects that timely completion and within budget. Payment rate would be $80 p/hr for project team and consultant pay is negotiable. |
| Constraints |
Disagreement among several employees with company’s new strategy. Consultant pay rates are also negotiable and it can be constraint. |
| Assumptions |
Initial investment in project is assumed to be
$90,000 and ROI is assumed to be 125%. |
Table 4: preliminary project requirements
Budget estimate (cost model and baseline)
| |
# Units/Hrs. |
Cost/Unit/Hr. |
Subtotals |
WBS Level 1 Totals |
% of Total |
| WBS Items |
|
|
|
|
|
| 1. Project Management |
|
|
|
$21,100 |
15% |
| 1.1 Project manager |
100 |
$50 |
$5,000 |
|
|
| 1.2 Project team members |
100 |
$80 |
$8,000 |
|
|
| Contractors (10% of software development and testing) |
|
|
$8,100 |
|
|
| 2. Hardware |
|
|
|
$9,000 |
6% |
| 2.1 Handheld devices |
60 |
$100 |
$6,000 |
|
|
| 2.2 Servers |
3 |
$1,000 |
$3,000 |
|
|
| 3. Software |
|
|
|
$73,750 |
51% |
| 3.1 Licensed software |
25 |
$150 |
$3,750 |
|
|
| 3.2 Software development* |
|
|
$70,000 |
|
|
| 4. Testing (10% of total hardware and software costs) |
|
|
$11,000 |
$11,000 |
8% |
| 5. Training and Support |
|
|
|
$16,550 |
11% |
| 5.1 Trainee cost |
60 |
$120 |
$7,200 |
|
|
| 5.2 Travel cost |
9 |
$150 |
$1,350 |
|
|
| 5.3 Project team members |
100 |
$80 |
$8,000 |
|
|
| 6. Reserves (10% of total estimate) |
|
|
$13,140 |
$13,140 |
9% |
| Total project cost estimate |
|
|
|
$1,44,540 |
|
Table 5: Budget
Budget of 145,000 has been decided for the project therefore all the necessary costs are allocated as per the current rates and resource requirement in budget. 10% of total estimate has would be kept as contingency reserve. Project management, hardware, software and training costs are included in budget. Major part of budget is going to be spent on hardware as it is crucial part of project.
Schedule estimate (including work breakdown structure level 3)

Scheduled estimates of all project activities have been shown in the image. Each activity has been allocated with estimated time for accomplishment. This organisation would help in managing work as schedule and priority. E marketing evaluation strategy is prime activity and other activities are supporting activities. These support activities would take place one after another.
List of potential risks
Potential risks are mentioned below:
- Resistance from employees to adapt with new policy. Lack of employee support can lead to failure of project.
- Changing market environment can affect the strategies and evaluation.
- Incorrect assumptions can affect the effectiveness of project.
- Increasing cost of resources can increase the budgeted cost for project.
- It is a time consuming process therefore it can take more than three months to complete the project.
- Conflicts regarding pay rates can be arise.
Conclusion
Thus it can be concluded that e commerce strategies in business help in reaching large number of customers in low cost. However these e commerce projects require time and cost. It can be seen from the case study that a project for evaluation of e marketing strategy has been proposed. There are various functions involved with project as budget, risks, financial analysis and recommendations. Return from investment in new project is expected to profitable and all the activities are allocated as per budget and time. There are risks of conflicts and disagreement during the project. It is also seen that activities are divided in work breakdown structure level three.
References
Chaffey, D., & Ellis-Chadwick, F. (2019). Digital marketing. Pearson UK.
Das, H. R., Rao, P. S., Kamath, G. B., & Prasad, H. S. (2019). Influence of E-Marketing Strategy on Customer Satisfaction. International Journal of Innovative Technology and Exploring Engineering, 8(9 Special Issue 3), 289-292.
Hollensen, S. (2019). Marketing management: A relationship approach. Pearson Education.
Noe, R. A., & Kodwani, A. D. (2018). Employee Training and Development, 7e. McGraw-Hill Education.
Panwar, R., Nybakk, E., Hansen, E., & Pinkse, J. (2017). Does the business case matter? The effect of a perceived business case on small firms’ social engagement. Journal of Business Ethics, 144(3), 597-608.
portfairycaravanparks.com. (2020). Port Fairy Caravan Parks | Quality Holiday Accommodation & Camping. Retrieved 4 May 2020, from https://www.portfairycaravanparks.com/
Wirtz, J., & Zeithaml, V. (2018). Cost-effective service excellence. Journal of the Academy of Marketing Science, 46(1), 59-80.
Abstract
Project management is the presentation of information, services, measures, and approaches applied to project actions so that the organization can fulfill essentials of the project. The history of the project management studies incorporates detailed growth in profession year by year. Project management methods are being used for decades while the documentation and the standardization took place later on for the customized projects. The history of project management methods’ has substantial value for choosing the right method on the right project.
Overview
Project
To understand the project management, “Project” needs to be clarified for better clearance on the project management.
A project can be short-term work started to create and develop a unique product, service, or outcome. Every project defines the work has a beginning and the end both. The beginning is where the idea is been generated and the end would be the result, is the objective of the idea is achieved and the existence of the project with the accomplishment or termination.
Project Management
Project management is the keyword implemented for the knowledge of implementation way for the success of any teamwork. Few studies says that this word “Project Management” is being used since the 19th century (Chofreh, et. al., 2016). Project management is an idea used by engineers and architects for long, it may be before civilization. Nowadays, Project management is an essential chunk of any organization to walk on the success path. It has immense specifications and details for the operation and fruitful achievement.
The old pyramids, The Great Wall of China, and Coliseum are the true models of project management. These unique structures are not been in existence without the people or team in charge of managing them. A study for the completion of vast projects showcases that the work had been assigned to different assemblies with different sorts to accomplish the task and achieve desired results. However, the outcome was not that strong in the imagination.
Antiquity
There is no perfect or solid evidence or documentation for the start of the project management. After researches and studies, the history of the Project management starts as follows:
- 2570 BC: The Great Pyramid of Giza’s structure
Emperors structured the pyramids and in present scenario the architects, studying and researching how they have managed to start the amazing monument, executed the idea and then attained the end of the project. This shows the project management skills in an earlier era (Chofreh, et. al., 2016).
- 208 BC: The Great Wall of China’s creation
Alternative wonder of the world, the planning, and execution of the project were organized by king by diving the team into three groups and thousands of people were ordered to help the construction team to comprehensive this huge project.
- 1917: The Gantt chart Established by Henry Gantt (1861-1919)
Founder and inventor of The Gantt chart, Henry Gantt created the scheduling diagrams on his name. The innovative idea is still considered as a vital part of the toolkit of project managers’
- 1956: The American Association of Cost Engineers (now AACE International) Formed
AACE was founded by experts of earlier times, project management and connected domains of designing and scheduling, estimation of cost, cost, and schedule control (Too & Weaver, 2014).
- 1957: The Critical Path Method (CPM) Developed by the Dupont Corporation
CPM formed by Dupont for the management of huge power plant maintenance. An approach to analyze timeframe of any project that is scheduling the task on plants along with the shutting downtime of plants while the project running.
- 1958: The Program Evaluation Review Technique (PERT) Developed for the U.S. Navy’s Polaris Project
PERT was designed special projects office which was element of department of defence of US Navy. It was known to be element of the Polaris mobile submarine-propelled ballistic missile project in times of the cold war (Silvius & Schipper, 2014).
- 1962: United States Department of Defence Mandate the Work Breakdown Structure (WBS) Approach
WBS created by the division of Defence as part of the Polaris mobile submarine-propelled ballistic missile project. It is an extensive, graded hierarchy organization of deliverables and work that must be executed to undertake a project
1965: The International Project Management Association (IPMA) Founded
First of the project management organisation is known to be IPMA. It was formed as a meeting for the link of project manager’s and sharing data (Pinto, 2014). Organisation is known to be federation of overall fifty domestic and globally based project management organisations and also it is authorised in Switzerland.
1969: Project Management Institute (PMI) Launched to Promote the Project Management Profession
PMI was known to be originated by five individuals as a non-for-profit entity and is dedicated to spread the practice, science, and project management as a profession. An article created by The Commonwealth of Pennsylvania for Merger for PMI in 1969, which was the authorised initiation.
1975: PROMPTII Method Created by Simpact Systems Limited
Structure of PROMPTII was basically for the computer projects as the projects were delayed over time investigated for execution and real budgets as mentioned in practicability studies (Silvius & Schipper, 2014).
- 1975: The Mythical Man-Month: Essays on Software Engineering by Fred Brooks
The book “software engineering and project management” by Fred Brooks, showcases fact “Addition of manpower to a late software project designs it afterwards.” This ideology is called law of Brooks’s.
1984: Theory of Constraints (TOC) Presented by Dr. Eliyahu M. Goldratt in his Novel “The Goal”
A clear sign on the title, TOC is a management viewpoint that supports any organization to successfully achieve the goals (Pinto, 2014). The TOC procedure searches to identify the limitation or obstacles in the projects and streamline the remaining of the organization’s tasks with application of Five Focusing Steps
1986 Scrum Named as a Project Management Style
Scrum is known to be an agile software development technique oriented on numerous small groups functioning in an exhaustive and mutually dependent form. ‘The New Product Development Game’ (Harvard Business Review, 1986) Takeuchi and Nonaka gave name as Scrum as a project management technique in their paper.
1987: A Guide to the Project Management Body of Knowledge (PMBOK Guide) Published by PMI
PMBOK is a guide for the standard tools and proper documentation of information and facts of project management practices. This guide is an essential tool in the project management profession since then it has become the globally used standard in the industry (Fleming & Koppelman, 2016, December).
1989: Earned Value Management (EVM) Leadership Elevated to Undersecretary of Defense for Acquisition
EVM framework was used in factory management systems since the early 19th century. EVM leadership was raised to the Undersecretary of Defense for Acquisition, thereby making EVM an primary aspect of programme management.
1989: PRINCE Method Developed From PROMPTII
PRINCE method was issued by the UK Government agency CCTA, PRojects IN Controlled Environments (PRINCE). It is known to be popular as the benchmark for all government system projects, a unique real approach, basically the ideology of ‘assuring development’ from three identical but connected views. Studies say, the measure is ungainly, too stiff, and applies only for the large projects.
- 1994: CHAOS Report First Published
The Standish Group formed for the collection of the information and details on any of the project failures in the IT industry (Panou, Mar 2018). The CHAOS report is the regular issue regarding IT project failure, this leads learning from the failure of others and discovering more methods to enhance on accomplishment rate and raising the worth of IT investments.
- 1996: PRINCE2 Published by CCTA
A second edition on PRINCE method, more standardized and applicable to any project announced by the primary computer and Telecommunications Agency), a UK government support agency. Initially established for Information Systems, and Information Technology projects to decrease overruns related to cost and time.
- 1997: Critical Chain Project Management (CCPM) Designed
CCPM was designed and introduced by Eliyahu M. Goldratt in 1997. The management of resources, keeping them in the proper level. This method is learning, keeping the resources flexible in start times and swapping among tasks when necessary to keep the project on a stable schedule. The method seems critical. However, it promotes the chain level project management system (Fleming & Koppelman, 2016, December).
- 1998: PMBOK Becomes a Standard
PMBOK was announced as standard for project management by The American National Standards Institute (ANSI) in 1997 and then afterwards it was recognized by the Institute of Electrical and Electronics Engineers (IEEE).
- 2001: The Agile Manifesto Written
Philosophy for Agile Software Development has known to be issued by developers of 17 software about the lightweight software development methods in their meet at The Lodge, Snowbird, Utah resort in Feb’2001.
- 2006: “Total Cost Management Framework” Release by AACE International
AACE introduced the idea for the entire cost management and issued the complete staging of the procedure in “Complete Cost management arrangement”. It has been introduced as a first integrated process, a method for application of the abilities and knowledge of cost engineering. Cost management is a significant slide in the project management system.
- 2008: 4th Edition of PMBOK Guide Released
The fourth updated version of PMBOK guide released with the PMI custom of superiority in project management with a standard that is more improved than earlier and convenient to comprehend and use with efficient reliability and enhanced organization (Ahola, et. al., 2014).
- 2009: Major PRINCE2 Revision by Office of Government Commerce (OGC)
A prime amendment in PRINCE2 made the approach easier to customize as per the user requirement. The updated version is classified into 7 principles, supports the success of the project.
- 2012: ISO 21500:2012 Standard for Project Management Released
After making research and investigation by analysts in more than fifty economies, book of the global entity for Standardization published “ISO 21500:2012, Guidance on Project Management” in September 2012.
- 2012: 5th Edition of PMBOK Guide Released
The next fifth edition of the book provides the enhanced version with strategies, regulations, and features for project management considered as noble practice or case studies in the profession of project management.
Importance of project management in modern world organizations
Project management is playing an important and crucial part for every size of organization for the management of day to day operations without any mess. It is now necessary for a company to hire a dedicated project manager to organize projects from beginning to achievement. Appropriate project management techniques are helpful for any organization to work on big projects, dealing budget and earning tag, reputation, success, and money (Ahola, et. al., 2014).
Few points are mentioned as below for the better understanding of the benefits using the Project management in the organization:
- Estimation: Project management promotes the core interest in any project with the estimate of the task involved like, time duration estimate, cost estimate, people required for the project estimate, a tool essential, and method or technology to be considered for the project.
- Planning: The Planning project is the heart of project management life rotation. The project plans are documented & the schedule is mentioned, which will result in delivering the preferred results.
- Exclusive Endeavour: The project management assists the organization to the successful achievement of the task for the unique product or service. The exclusiveness is never a temporary phase for the product managers, it is under the core job preferences.
- Timeline Review: forming a project, will never be without a specific timeline. The project management methods are used for the calculation of the timeline of the project.
- Budgeting: The project budget has significant importance in the project management of the task as any project can’t be even in the execution phase with the cost estimation or a budget approved (Joslin & Müller, 2015).
- Changes & Excellence: Both terms are significant for any organization as project management plays a key role to accomplish the changes as per the demand and skill developed manger acquired the methods to control the quality at the same time, to endure the happy customers.
- Opportunity: The wider projects may involve more planning, careful coordination, huge finances, long term project duration but it will ensure the futuristic and the extended tenure for the company’s success pathway.
Conclusion
Project management is a practice or skill that can be developed for the achievement of any task with proper planning, time duration calculation, budget estimation, upcoming changes, maintaining the quality with the opportunity and challenges. This required the optimum utilization of resources and applying inputs for the anticipated and unique outcome. Good project management guarantees that the goals of projects lined up suitably with the planned goals of the organization. The basis on the referral history of project management growth and enactment of methods in several years, project management is the core and essential part of any organization, group, or anyone performing task whether it’s a small or huge project. These methods show the clear path for the planning, execution and conclusion with the mandate consequences. The history of the project management exhibit the ideas, concepts and the skills ascended by researchers and learners for the improved accomplishment of the project management profession.
References
- Seymour, Tom & Hussein, Sara Minot State University, USA, The History of Project Management, 2014 https://www.researchgate.net/publication/298341808_The_History_Of_Project_Management
- Berkun Scott, O’Reilly Media, Inc. (Mar 2008) Making things happen Chapter 1. A brief history of project management (and why you should care) https://www.oreilly.com/library/view/making-things-happen/9780596517717/ch01.html
- Panou, George (Mar 2018 ) History and Processes of Project Management https://medium.com/@gpanou/history-and-processes-of-project-management-1ae31fa450eb
- A Brief History of Project Management https://vabotu.com/a-brief-history-of-project-management/
- https://certbuddyz.com/significance-of-project-management-in-modern-day-organizations/
- Silvius, A. J., & Schipper, R. P. (2014). Sustainability in project management: A literature review and impact analysis. Social Business, 4(1), 63-96. Available at: http://www.academia.edu/download/36896675/document11.pdf
- Too, E. G., & Weaver, P. (2014). The management of project management: A conceptual framework for project governance. International Journal of Project Management, 32(8), 1382-1394. Available at: https://mosaicprojects.com.au/PDF_Papers/P162_The_Management_of_Project_Management_IJPM.pdf
- Pinto, J. K. (2014). Project management, governance, and the normalization of deviance. International Journal of Project Management, 32(3), 376-387. Available at: https://www.researchgate.net/profile/Jeffrey_Pinto/publication/260295571_Project_management_governance_and_the_normalization_of_deviance/links/5b7d6b67299bf1d5a71c5030/Project-management-governance-and-the-normalization-of-deviance.pdf
- Fleming, Q. W., & Koppelman, J. M. (2016, December). Earned value project management. Project Management Institute. Available at: http://anclasol.com/AS/e-books/ing/FREEeBooks/earned%20value%20project%20management.pdf
- Ahola, T., Ruuska, I., Artto, K., & Kujala, J. (2014). What is project governance and what are its origins?. International Journal of Project Management, 32(8), 1321-1332. Available at: https://www.researchgate.net/profile/Jaakko_Kujala/publication/266619609_What_is_project_governance_and_what_are_its_origins/links/59db52190f7e9b2f587fd785/What-is-project-governance-and-what-are-its-origins.pdf
- Chofreh, A. G., Goni, F. A., Ismail, S., Shaharoun, A. M., Klemeš, J. J., & Zeinalnezhad, M. (2016). A master plan for the implementation of sustainable enterprise resource planning systems (part I): concept and methodology. Journal of Cleaner Production, 136, 176-182. Available at: https://www.researchgate.net/profile/Abdoulmohammad_Gholamzadeh_Chofreh/publication/303690262_A_master_plan_for_the_implementation_of_sustainable_enterprise_resource_planning_systems_part_I_Concept_and_methodology/links/5b44d7be458515b4f660288e/A-master-plan-for-the-implementation-of-sustainable-enterprise-resource-planning-systems-part-I-Concept-and-methodology.pdf
- Zou, W., Kumaraswamy, M., Chung, J., & Wong, J. (2014). Identifying the critical success factors for relationship management in PPP projects. International Journal of Project Management, 32(2), 265-274. Available at: https://core.ac.uk/download/pdf/38025795.pdf
- Alias, Z., Zawawi, E. M. A., Yusof, K., & Aris, N. M. (2014). Determining critical success factors of project management practice: A conceptual framework. Procedia-Social and Behavioral Sciences, 153, 61-69. Available at: https://www.sciencedirect.com/science/article/pii/S1877042814054834/pdf?md5=0c37253fda61413e1eddbb8df1cb25dd&pid=1-s2.0-S1877042814054834-main.pdf&_valck=1
- Joslin, R., & Müller, R. (2015). Relationships between a project management methodology and project success in different project governance contexts. International journal of project management, 33(6), 1377-1392. Available at: https://shop.tarjomeplus.com/UploadFileEn/TPLUS_EN_4093.pdf
Selected Job Profile
Cybersecurity analyst
Role: The role of the cybersecurity specialists is to maintain the security of the computer information systems majorly against cybercrimes that involve denial of service attacks, phishing sites, viruses, hacking, and malware. The roles and responsibilities of the cybersecurity analyst includes a number of activities to take care of, some of them are mentioned below:
- Generating reports for technical as well as non-technical shareholders.
- To track and respond to “pharming” activity and ‘phishing’ emails and websites.
- To keep updated with the latest technology and security developments.
- Research about emerging risks about cybersecurity and methods to handle those threats.
- Monitor attacks, unusual activities, intrusions and unauthorized or illegal activities.
- Give guidelines and advice to the staff on issues such as unwanted or malicious and spam mails.
- Make plans for disaster recovery while security breaches.
- Help with the maintenance, creation, as well as delivery of awareness trainings about cyber security to the colleagues.
- Evaluate and test for the security products.
- Upgrade existing security systems by designing the new security systems.
- Engaged in Ethical Hacking for simulating security breaches.
- Investigating security alerts and provide response.
- Identifying potential weakness in the system and implement measures accordingly such as firewalls and encryptions.
- Monitoring identity and access management.
Qualifications
It is not necessary to have a degree to enter this profession of cyber security analyst. You just have to be skilled enough to work up to cyber security role.
Majority of the employer recruit for a position of a graduate, they prefer or require, a graduate degree in science or technology or may be in Engineering (Narayanan, et al., 2017).
Exact requirements may vary from employer to employer. More relevant degree subjects include:
- Computer science
- Information security
- Network Engineering
- Information security
- Network security
- Information technology
- Software Engineering
Your degree will not value any longer as once you start gaining experience, and the employers will be interested in what projects you’ve worked upon, not in your qualification. You may choose relevant subject area to undertake further studies.
Some employers can sponsor you to undergo relevant master’s degree. You can also choose a certification related to cyber security to get a proof of a knowledge you’ve gained.
Career Prospects
Cybersecurity is one of the rapidly developing field and currently there is a skill shortage. Job scope is good for the skilled and experienced people. One will start with an entry or junior level cyber security job. After gaining the experience of several years you could get progress into senior cyber security roles like cyber security analyst/ cyber security consultant (Palmer, et. al., 2019).
After having a significant expertise in the same field, one might be able to get progress in high level leadership roles as well as managerial roles, and eventually ending up with becoming a head or director of cyber-security. Achieving certifications relevant to the cyber security might be help in your development as most employer consider these roles as important.
Self-employment can be considered as a choice, but mostly people firstly gain expertise in the relevant field. one could set a company which will provide cyber security services or can individually work as independent cyber security consultant.
Application letter
Dear Mr. XYZ
PQR security Consulting
Sub: Job Application
Sir,
I am looking for a job in field of cyber security analyst in a reputed company and I would like to work in your company. I think I have all necessary skills along with experience required by your company and would be glad to make valuable contribution in success of your company. As indicated by my resume I have more than 5 years of experience in field of cyber security. I have worked as team leader in national division of cyber security for more than 3 years and has done many projects as an analyst of cyber security. I have earned my degree of bachelor in field of computer science with very strong mathematical background. Previously I was working in division of national cyber security for so many years I have learned many things there and gained experience in many fields such as how we can secure any computer system like large server, and mainframe, from external as well as internal attacks. This is an obvious thing that analyst of cyber security needs continuous education about field with time because there are a lot of hackers can be seen in world and they keep finding new methods of infiltration of computer systems. An analyst of cyber security must stay ahead of them from one step so that they can’t infiltrate computer systems easily.
My main strengths lie in effectively leading a team and problem solving and I accepts challenges created by hacker to get into my computer system very gladly and I always stay ahead of them. I have strong communication skills required for leading a team and along with that my English is good so that I will not find any troubles in making necessary reports and documents. I have sharp analytical skills and can solve very complex problems easily. I have very good time management skills and able to meet deadlines for assigned projects. I can assist staff in errors understanding and glitches repairing. I have excellent knowledge about use of computer programs aiming in direction of digital security. I will love opportunity of working in your company as analyst of cyber security.
I am very certain that your company will find all of my talents and expertise up to the mark for an analyst of cyber security. Please schedule an interview according to your convenience I am expecting a person to person or a telephonic interview to be scheduled as soon as possible. I am excited to meeting you and to work in your company and I also thank you for your valuable time and for your considerations.
Sincerely,
XYZ
Major criteria of selection
Key criteria of selection in any company as an analyst of cyber security some major points must be kept in mind and there are some basic as well as advanced requirements like licensing requirements, experience, education requirements etc. for working as analyst of cyber security in any company. All these requirements are mentioned below with full description:
- Person’s bachelor’s degree must be in field of computer science or in field of information system or there can be equivalent work experience or education (Washington, 2017).
- Experience should be more than 4 years. In field of cyber security with good mathematical background.
- Person must have done advanced certification courses such as GCIA, SANS GIAC, GCIH, CASP or CISSP and special training of SIEM along with certification.
- Certification of Hold DoD 8570 IAT of 2nd level (CE + Security) at date of starting.
- An analyst must have advanced understanding in fields of TCP/IP, Basic networking
- Protocols and ports, flow of traffic, administration system, OSI model, in depth defence and elements of common security.
- High level of experience in analysing high-volume logs, network’s data and many other artifacts of attack in incident investigation’s support.
- Experience in scanning solutions of vulnerability.
- Familiarity in program of vulnerability program of DOD information’s assurance.
- Good knowledge of any of following: HIPS, anti-virus, complete packet capture, ID/PS, forensics which are host based, forensics of network, and security of RSA.
- Complete and in-depth architecture knowledge, knowledge of engineering, and all operations of minimum 1 enterprise ‘s SIEM platform (for e.g. Nitro or McAfee manager of enterprise security, Radar, Log Logic, ArcSight, Splunk.
- Experience in deploying along with developing signature. (e.g. Snort, YARA, HIPS, Suricata).
- Complete understanding of Operating system (i.e. IOS, Android, Windows) and mobile technology along with VMware technology, and basic Unix commands with Unix.
Skills required for cyber security
- System administration: An analyst of cyber security must posses’ skills of managing so many systems such as software, hardware, workstations, effectively and efficiently.
- Network security: an analyst of cyber security must have ability to protect underlying infrastructure of networking from misuse, malfunction or unauthorized access. So that a secure and safe platform can be created for all computer systems (Piplai, et al., 2019).
- Problem solving: cyber security officer must posse’s skill of problem solving as hackers always try to infiltrate systems with new techniques and an analyst must have solutions of these problems.
- Policies of information security: these are some rules that formed by a particular organization to ensure all networks and users of IT structure within company can stay secured.
- Firewall administration: firewall can be defined as a device for network security which control network traffic and decide which traffic to be allowed or which is to be rejected on based of defined rules for network security.
- Network protocols: network protocols can be defined as policies or standards made by rules, formats, procedures, that define communication in between devices over any network.
- Routers, switches, hubs: Hubs can be defined as dumb devices that have ability to pass one to other connections. Switches can be defined as semi intelligent device that knows which device has which connection, routers are very intelligent and can perform many tasks.
- Process improvement: it can be defined as a task of identifying, analysing and after that improving business processes which were not that good previously. This must be done for optimization of organization and to reach to new quality standards.
Curriculum Vitae
ABC
Cyber Security Analyst
Phone: (0123) 456789 | XXX@gmail.com | Website: demo.com
SUMMARY
Verified Cyber Security Analyst having more than 6 years of expertise in system security, intelligence, security operations and cyber-crimes investigator. Skilled in risk assessment and handling, Risk Management Framework (RMF), vulnerabilities handling, Assessment as well as Authorization. Can efficiently interact with a number of different individuals, agencies, interests and constituencies.
CORE COMPETENCIES
Network Administration of TCP/IP, Penetration Testing, Antivirus, Antimalware, Vulnerability Scanning, Network Security, Framework Assessment, Snort and Nessus Risk Management, POAM Management, Authorization and Authentication, NIST, CSAM, FISMA, Firewall, FIPS Security Control Assessment and prevention Protocols/ Intrusion Detection, Mainframe, Windows, Linux and Unix Operating Systems, Packet Analysis Tools and Network Protocols.
PROFESSIONAL EXPERIENCE
Cyber Security Analyst
Lookout June 2013 – Present
Key Deliverables:
- Interviewing system admins and other shareholders in support of the AA process to assist in generating personalized reports and/or artefacts.
- Identifying security checks and building a compliance matrix for monitoring.
- Apply adequate Federal Information System Cyber Management Regulation focused on NIST 800-37, analyse risks and weaknesses based on realistic studies.
- Supports us by protective cyberspace operations (DCO) with cyber guidance and central command (Centcom).
- Performing as the Cyber Protection Team Reduction Squad (CPT) information-security analyst within the network security divisions.
- Protects essential assets and main services inside the global knowledge system agency for security.
- Providing protection assistance to FISMA and Nist process information system security officers (Isso), and touch level.
- Implement security assessment as well as authorization environments like network protection categorization, safety and contingency plan creation, security testing & review, device accreditation, and ongoing tracking.
System Support Engineer
Crowdstrike January 2012 – May 2013
Key Deliverables:
- Undertakes all-source information review of the strengths and risks of adversarial cyberspace by investigation and study.
- Researching, preparing, deploying, configuring, troubleshooting, updating and improving operating systems.
- Diagnose the problem and fix issues with equipment, applications, and networking including device control and synchronization of devices.
- Computer equipment and peripherals mounted, programmed, and modified to also include the network card, scanners, modems, and add-in panels.
- Imaged machines and network administration tools utilized for ticketing services support desk.
- Addressed remedial steps to prevent intrusion identification and destruction of viruses, and malware.
- Helping consumers define the problems through the use of the information base.
- Provide technical assistance of the information network to a broad variety of clients in industrial national security settings.
- Provide technical assistance to a broad variety of users in the industrial information security field via the computer network.
- Use predictive technology to track network irregularities and harmful communication.
- Use predictive technology to track network irregularities and harmful communication.
- Help for the deployment and troubleshooting of desktop and portable devices on Linux, macs, android, Windows computers, and iOS handheld apps; problem / incident reporting, and problem / scaling.
- Using advanced analytics discover anomalies in networks and malicious traffic.
EDUCATION
Master of Science May 2016(Malborne University, School of Graduate &
Professional Studies , MD)
References
Narayanan, S. N., Ganesan, A., Joshi, K., Oates, T., Joshi, A., & Finin, T. (2018, October). Early detection of cybersecurity threats using collaborative cognition. In 2018 IEEE 4th international conference on collaboration and internet computing (CIC) (pp. 354-363). IEEE.
Piplai, A., Mittal, S., Joshi, A., Finin, T., Holt, J., & Zak, R. (2019). Creating cybersecurity knowledge graphs from malware after action reports.
Palmer, C., Angelelli, L. A., Linton, J., Singh, H., & Muresan, M. (2016, September). Cognitive Cyber Security Assistants—Computationally Deriving Cyber Intelligence and Course of Actions. In 2016 AAAI Fall Symposium Series.
Washington, T. (2017). Critical Skill Job–Cyber Security Analyst. Savannah River Site (SRS), Aiken, SC (United States).
Individual Analytic Report
Executive Summary
Data is an essential asset which helps in creating the competitive advantages over organization. Data Analytics helps organization develops operational efficiency, drive new income, & increase competitive advantage. In this report, how data analytics provides business to users or organizations has been discussed by choosing the SPSS tool. SPSS is termed as Statistical package for the Social Sciences which are use to solve difficult statistical data analysis. SPSS issued by market researchers, health researchers, marketing organizations, & many more for analysing the data. In this report two types of data analytics can be discussed i.e., predictive & prescriptive, Why SPSS tool in data analytics will be chosen & why it is used & the improvements to the data analytics to user or organization by using SPSS tool has been further discussed in assignment. For improving the business growth of any organization, it needs to collect related information.
Research Question
How can data analytics provide (business) value to users &/or organisations?
Introduction
The report includes the details about the data analytics done in the business. The report includes the detail about the importance of the data analytics to the users & the organisation. The software used in this report for the data analytics is the SPSS solutions. The SPSS solutions are the software package that is used for the interactive statistical analysis that is done in the business or organisation. The current name of the SPSS tool is the IBM SPSS Statics. This tool is used by the large number of the organisation for the statistical analysis in social science. The SPSS statistics focuses on simplifying the programming by including the internal file structure, data processing, data type etc. this tools used by the various researchers in making the statistical analysis of the data. The programs offered by the SPSS tool are statistics programme, modeller programme, visualisation designer & text analytics for survey programs.
Importance of data analytics
Data analytics is important to the business & the users. Data analytics is needed in the business to consumer applications (Devi et. al., 2013). The organisation collects the data from the consumers & then this data is gathered & categorised after this the analysis is done. The data analytics will help the business to grow. Therefore, it can be said that there is certain factor that can define the importance of data analytics in the business such as:
Analysis of business value chain
The data analytics helps the business to analyse the ways in which the existing information can be used to help the business in finding the way to the success.
Industry knowledge
The data analytics helps the business to gain the knowledge about the industry. In this the business can get the knowledge about the ways they can adopt to succeed in future (Chen et. al., 2012). It also helps to analyse the economy that is avail bale with the business.
Seeing the opportunities
The data analytics helps the business in analysing the data that can help in creating the opportunities for the business. It is said to be the way of unlocking the various options for the business.
It benefits the users as they can get the collected data in the systematic form that can help them in making the decision easily. Therefore, it can have said that the data analytics benefits both the users & the organisations & provides various facilities to them.

(Source: digitalvidya.com)
Executives of chosen data Set- Predictive & Prescriptive
Predictive analytics
Predictive analytics help to link data to successful action by representation dependable conclusions about current events & situations (Arkkelin, 2014). This helps in organization to practical in cutting cost, reducing risk & increasing profitability, optimizing their business & driving latest form of business.
The SPSS predictive analytics software used for:
- Transform data into predictive approaching to direct frontline choices & interactions.
- Predict what consumers want & will do further to enhance profitability & retention (Ayhan, et. al., 2013).
- Increases efficiency of the individual, process & resources.
- Identify & avoid threats & frauds before they influence the association.
- Determine social media effect of the products, services & marketing campaign.
- Execute statistical analysis as well as regression analysis, cluster analysis & correlation analysis (Agudo-Peregrina, et. al., 2014).

(Source: IBM, 2019)
Prescriptive analytics

(Source: DSC, 2019)
Prescriptive analysis can used to find out the best solution or results with all choices, given the recognized parameters (Vajjhala, et. al., 2015). When combined the predictive analytics, the prescriptive analytics can recommend result option for how to take benefit of future prospect or moderate upcoming risks. This analytics gives vast value to planners & decision makers .The main reason of the prescriptive analytics is not still widely used in difficult planning processes is that frequently these processes are exceptional to the organization. The accessible SPSS tools that previously offer superior planning together with prescriptive analytics don’t manage well among these business particulars (Keahey, 2013). It improves operations, reduces risk & mange resources efficiently.

Fig: Afghanistan Marital Status for men and women
Why it is used & why it is chosen or laid out in fashion
SPSS was chosen due to its ubiquity within equally scholarly & business circles, building it the most generally used collection of its type. SPSS is similarly flexible packages that permit a wide variety of kinds of investigation, information change, & types of give up in short; it will further than satisfactorily fill their requirements (Sun, et. al., 2014). SPSS tool is utilized for both subjective & quantitative investigation can be examined by the product along these lines making the specialists work simpler. In this way, why SPSS is significant in information examination can’t be undermined since it has altered the information investigation process.
To condense what they have canvassed in this section, they will advance throughout accompanying strides as you make & execute a SPSS program:
- Access SPSS for Windows from PC hard drive or from system (LAN)
- Create an information record in SPSS Data Editor or SPSS Syntax Editor
- Save information record utilizing suitable document expansion (.SAV or .SPS)
- Specify an investigation to be kept running on information document (e.g., Frequencies)
- View consequences of an examination in SPSS Viewer Window
- Save yield record in this Viewer Window utilizing the SPO document amplification (Schoenherr & Speier‐Pero, 2015).
Practical Approach

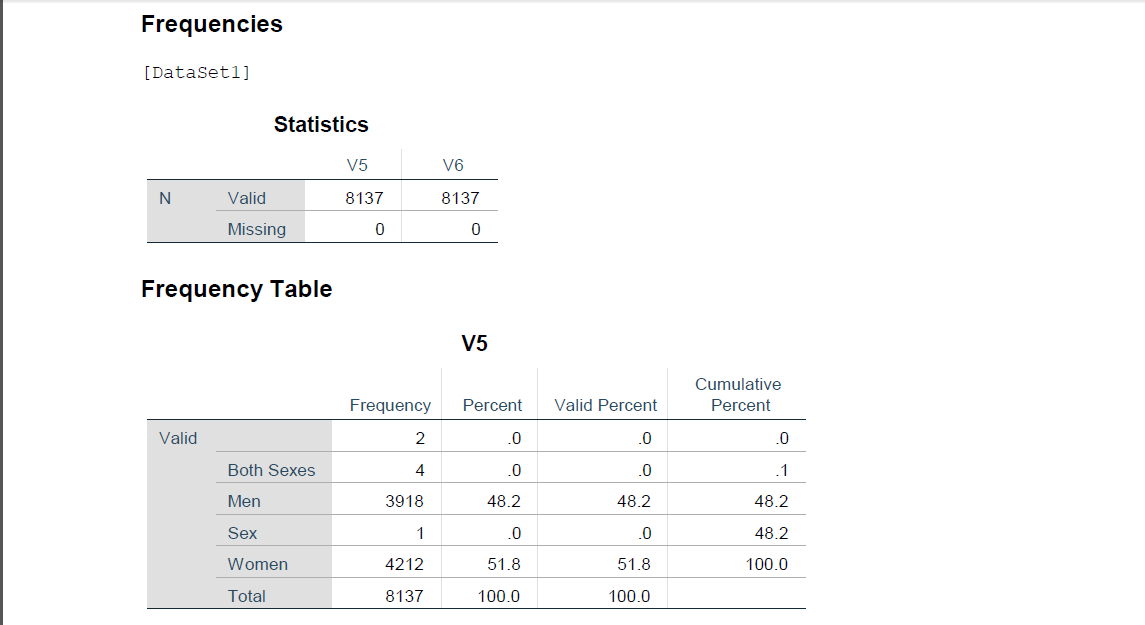





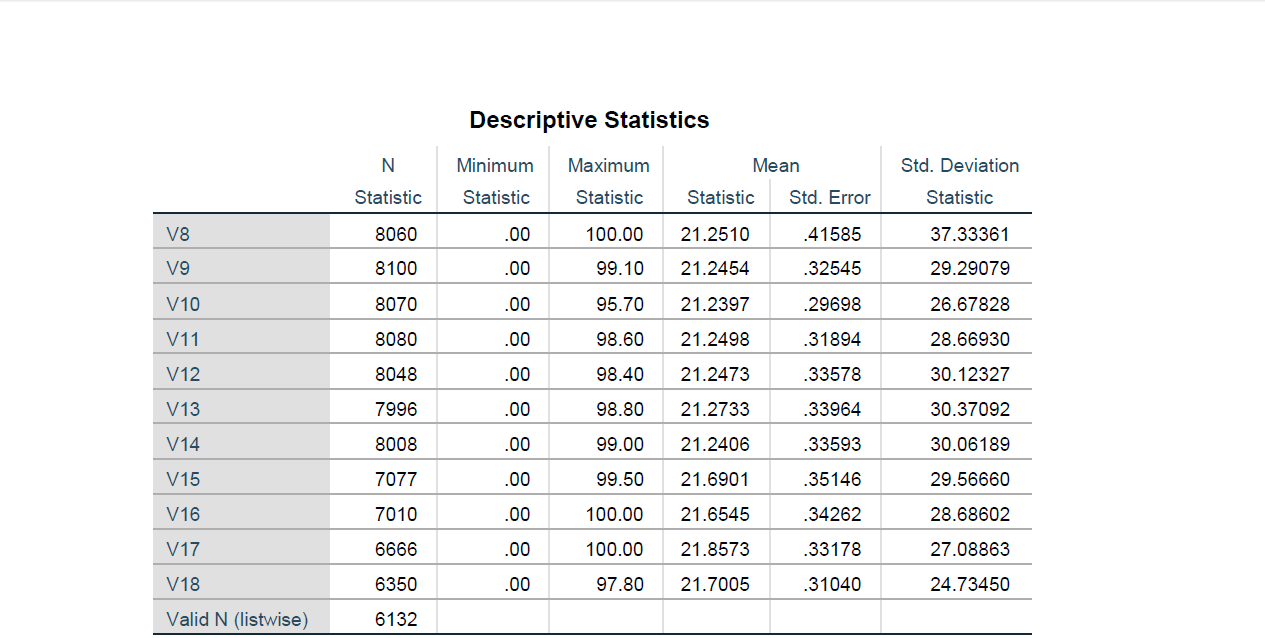
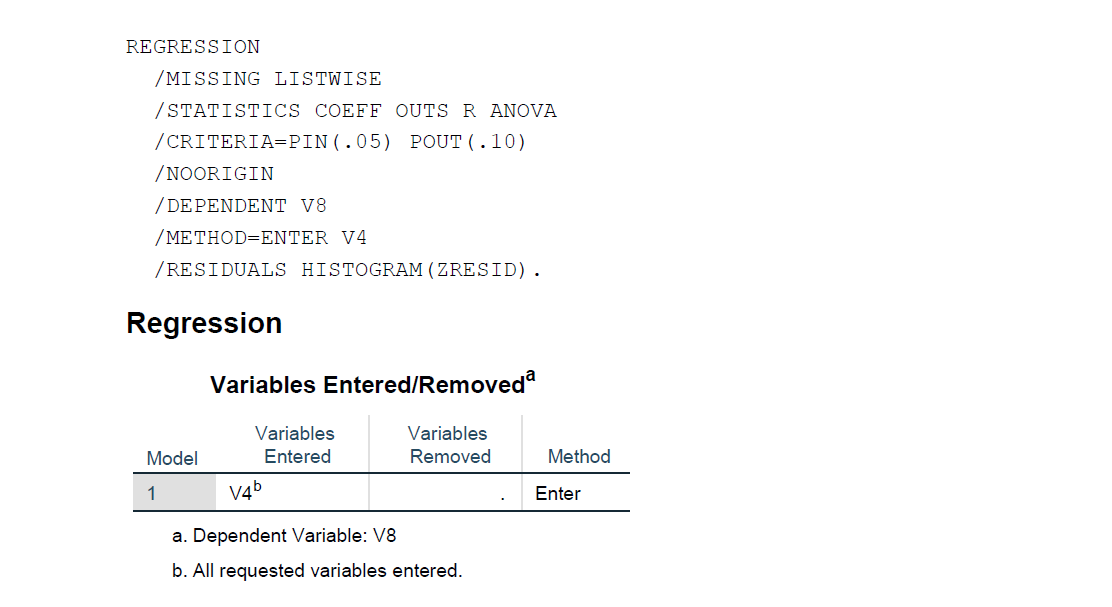


Improve the operations
The CEO wants to improve the operations, the use of the tool SPSS solutions can help to improve or enhance the sale & operations of the company. The CEO should use the predictive analysis of the tool so that can help in predicting the outcomes, make smarter decisions & getting the better results for the company. The improvement can be made by the company by saving the money through the predictive analysis. Therefore, it can be said that the predictive analysis can help the business in saving the money (Duan & Xiong, 2015). The operation can be improved by avoiding the costly problems that can occur in the operations. This can be done as the SPSS tool can help in predicting the operating characteristics of the business cost effectively & accurately that can help in analysing the factors that can generate the downtime or the benefits to the business. Another through which the operations can be improved by the CEO using this software, as the predictive analysis can impact the profitability & the competitiveness of the organisation. The predictive analysis through this tool can help the business in to turn the vast amount of structured & unstructured data into actionable one. Therefore, through this it can be seen that there are various ways that can be used by the business to improve the operations & increase the sales of the business through the use of the SPSS solution tool.
Conclusion
Through this report it can be concluded that the tool that has been used for the data analytics is the SPSS solutions. It is the best tool as it can help to improve or enhance the sale & operations of the company. Data analytics is important to the business & the users. The data analytics helps the business to analyse the ways in which the existing information can be used to help the business in finding the way to the success. The report includes the details about the data analytics done in the business. The report includes the detail about the importance of the data analytics to the users & the organisation.
References
- Agudo-Peregrina, Á. F., Iglesias-Pradas, S., Conde-González, M. Á., & Hernández-García, Á. (2014). Can we predict success from log data in VLEs? Classification of interactions for learning analytics and their relation with performance in VLE-supported F2F and online learning. Computers in human behavior, 31, 542550. Retrieved from: https://www.sciencedirect.com/science/article/pii/S074756321300188X
- Arkkelin, D. (2014). Using SPSS to understand research and data analysis. Retrieved from: https://scholar.valpo.edu/cgi/viewcontent.cgi?article=1000&context=psych_oer
- Ayhan, S., Pesce, J., Comitz, P., Sweet, D., Bliesner, S., & Gerberick, G. (2013, April). Predictive analytics with aviation big data. In 2013 Integrated Communications, Navigation and Surveillance Conference (ICNS) (pp.113). IEEE. Retrieved from: https://ieeexplore.ieee.org/abstract/document/6548556
- Chen, H., Chiang, R. H., & Storey, V. C. (2012). Business intelligence and analytics: From big data to big impact. MIS quarterly, 36(4). Retrieved from: https://pdfs.semanticscholar.org/f5fe/b79e04b2e7b61d17a6df79a44faf358e60cd.pdf%3E.
- Devi, B., Rao, K., Setty, S., & Rao, M. (2013). Disaster prediction system using IBM SPSS data mining tool. International Journal of Engineering Trends and Technology (IJETT), 4, 33523357. Retrieved from: https://www.statwks.com/wp content/uploads/2019/03/Disaster-Prediction-System-Using-IBM-SPSS.pdf
- Digitalvidya, (2019). About us. [Online] Digitalvidya. Available at: https://www.digitalvidya.com/wp-content/uploads/2017/04/Data-Science.png . [Accessed: 17 September 2019].
- DSC, (2019).Welcome to data science central. [Online] DSC. Available at: https://www.google.com/url?sa=i&source=images&cd=&cad=rja&uact=8&ved=2ahUKEwiy7fKQ7tfkAhWDdn0KHfOKBnIQjhx6BAgBEAI&url=https%3A%2F%2Fwww.datasciencecentral.com%2Fprofiles%2Fblogs%2Fprescriptiveanalytics&psig=AOvVaw3fKTPyYBGqKs43SuwBVZH4&ust=1568809754870048.[Accessed: 17 September 2019].
- Duan, L., & Xiong, Y. (2015). Big data analytics and business analytics. Journal of Management Analytics, 2(1), 1-21. Retrieved from: https://vivomente.com/wp-content/uploads/2016/04/big-data-analytics-white-paper.pdf
- IBM, (2019).About us. [Online] IBM. Available at: https://www.google.com/url?sa=i&source=images&cd=&cad=rja&uact=8&ved=2ahUKEwiVnr27dfkAhUJ7XMBHeRoAiUQjhx6BAgBEAI&url=https%3A%2F%2Fwww.ibm.com%2Fdeveloperworks%2Fcommunity%2Fblogs%2Fibmbi capabilities%2Fentry%2Fpredictive_analytics_with_ibm_spss_basic_q_as&psig=AOvVaw3kjIHcJcM0v5ZMt9I6yyWh&ust=1568809598168726. [Accessed: 17 September 2019].
- Keahey, T. A. (2013). Using visualization to understand big data. IBM Business Analytics Advanced Visualisation. Retrieved from: https://dataconomy.com/wpcontent/uploads/2014/06/IBM-WP_Using-vis-to-understand-big-data.pdf
- Schoenherr, T., & Speier‐Pero, C. (2015). Data science, predictive analytics, and big data in supply chain management: Current state and future potential. Journal of Business Logistics, 36(1), 120132. Retrieved from: https://onlinelibrary.wiley.com/doi/abs/10.1111/jbl.12082
- Sun, N., Morris, J. G., Xu, J., Zhu, X., & Xie, M. (2014). iCARE: A framework for big data-based banking customer analytics. IBM Journal of Research and Development, 58(5/6), 4-1. Retrieved from: https://ieeexplore.ieee.org/abstract/document/6964895
- Vajjhala, N. R., Strang, K. D., & Sun, Z. (2015, August). Statistical modeling and visualizing open big data using a terrorism case study. In 2015 3rd International Conference on Future Internet of Things and Cloud (pp.489496). IEEE. Retrieved from: https://ieeexplore.ieee.org/abstract/document/7300857
Introduction
In this article summary, the questionable research practices have been explained as analytic, design or reporting operations that have been questioned because of the possibility for the operation to be engaged with the motive of today influenced proof in approval of a declaration. In the present review, four primary types of proof are considered.
Summary
QRP description
QRP was mention in the 1958 code of professional ethics and operations of public opinion researchers. In this, they defined upon members to accept the standards forced everywhere by the science of man. Never pamper to knowingly questionable research practices in context to reach some previously arranged result or demonstrate a case. Nowadays or the present study gives an idea about the four types of proof that are considered.
Proof from behavioral observations
An ordinary technique is utilized in behavioral observation studies of QRP’s is to collate research agreements or versions that are earlier studied. For example; conference, dissertation paper. The aim is to see if there are baseless results. Additionally, someone can also collate, anyway or not behaviours like the reducing of data and add or reducing control variables were related to the moving a not particular result into a specific one. The behavioral observation approach gives an advantage is that someone does not have to be worried about the possibility for influence reporting due to social appeal as is the case when observer and self-description surveys are utilized.
Proof from sensitivity examines
This can be utilized to assess the committing in QRP’s by computing the expectation that a set of outcomes is possible. As compared with the behavioral approach this analysis has limitations and strengths. For example, sensitivity analysis does not need researchers to answer reliably on questions which are occurred. Also, researchers do not depend on the respondent’s past behavioral memories. These analyses are not worried about with the researchers justifies this type of behaviour. But sooner centralized on a statistical probability evaluation. Based on dissimilar behavioral approach there are one advantage of this analysis is that they do not need rules and regulations or early drafts of a study in the context of investigation operational in QRP’s.
Proof from self-report surveys
By the use of these surveys to investigate QRP’s has various methodological strengths and limitations. Based on the priority to give the degree of autonomy and choice researchers have, this gives a great opportunity to grab in suboptimal practices of research. In numerous cases, it is not likely that even co-authors would be aware if not appropriate techniques were being utilized to operating results. What are the methods to recognize engagement in QRP’s that not else be commented on? These surveys are may also utilize to investigate the area to which engagement in QRP’s is unsettled to authors’ violations collated to reviewer and reviser request in the process of review.
Proof from surveys of observer report
As discussed previously methodological proposals, also have limitations and strengths to using report surveys of the observer to study engagement in QRP’s. Sometimes many QRP’s may happen that cannot be recognized by behavioral observations or sensitivity analysis. Compare with the self-report surveys one advantage of observer reports is that they can excavate those QRP’s that can only be deliberate by requesting researchers what happened behind the scenes of the data analysis, collection and results report (Verhees, 2020).
Conclusion
The present study managed a search of publications on the methodological design, reporting and analytic of research practices that put a question in nature. All study gives an overview that is limitations are associated with the different ways they employed. Based on the analysis conclusion has achieved that it is not likely that most researchers attract in QRP’s each time study is again conducted.
References
Verhees, V. 2020. Blind regression analysis to counter p-hacking in psychology (Master’s thesis). Available at: https://openaccess.leidenuniv.nl/bitstream/handle/1887/85349/Verhees%2C%20Veronique-s2311895-MA%20Thesis%20MS-2020.pdf?sequence=1